This research report has been funded by Radworks. By providing this disclosure, we aim to ensure that the research reported in this document is conducted with objectivity and transparency. Blockworks Research makes the following disclosures: 1) Research Funding: The research reported in this document has been funded by Radworks. The sponsor may have input on the content of the report, but Blockworks Research maintains editorial control over the final report to retain data accuracy and objectivity. All published reports by Blockworks Research are reviewed by internal independent parties to prevent bias. 2) Researchers submit financial conflict of interest (FCOI) disclosures on a monthly basis that are reviewed by appropriate internal parties. Readers are advised to conduct their own independent research and seek advice of qualified financial advisor before making investment decisions.
Securing DeFi: Frontend Security Infrastructure and User Behavior in Web3 Applications
Key Takeaways
- Infrastructure Vulnerability Creates Systemic Risk: The DeFi ecosystem exhibits a core architectural problem where protocols execute on censorship-resistant blockchains while relying entirely on centralized frontend delivery infrastructure, creating concentration risk that has materialized in significant losses.
- Market Opportunity Exists in the Security Protection Gap: Our primary research reveals 88% of users prioritize frontend vulnerabilities as their top concern, yet only 41% implement comprehensive protective measures. Additionally, 55% indicate they would increase DeFi activity given enhanced frontend security, suggesting material potential for effective security solutions.
- User Friction Tolerance Defines Critical Design Constraints for Security Solutions: Market adoption hinges on minimizing implementation friction, as 59% of users will only accept one additional click or step for enhanced security while 95% demand direct access via official protocol frontends.
- Radworks Positioned to Capture Emerging Enterprise and Institutional Demand: Protocol teams are actively planning migration from centralized hosting infrastructure while regulatory evolution demands operational resilience, positioning Radworks to capitalize on immediate B2B opportunities.
Introduction
DeFi protocol infrastructure has a fundamental problem: smart contracts operate on decentralized blockchains, yet users access them through centralized web frontends that present significant attack vectors. These vulnerabilities have proven costly: the Badger DAO Cloudflare compromise resulted in $120 million in losses, while Curve Finance suffered a DNS hijacking attack. SlowMist data shows $494 million lost to phishing attacks in 2024, with frontend exploits representing a substantial portion.
We conducted primary research with high net worth individuals, institutional investors, finance professionals, and leading DeFi protocol teams to analyze current security practices and quantify market demand for decentralized frontend solutions and security tools. Our findings evaluate user behavior patterns, infrastructure requirements, and commercial opportunities for solutions like Radworks’ decentralized frontend launcher.
The DeFi Frontend Security Landscape
Attack Vector Evolution
Frontend attacks exploit the disconnect between decentralized protocols and centralized web delivery. Unlike smart contract exploits requiring code vulnerabilities, frontend exploits target traditional web infrastructure through established attack vectors adapted for blockchain interactions.
DNS hijacking redirects domain queries (a request to a server for an IP address) to attacker-controlled servers, replacing legitimate interfaces with malicious copies. The Curve Finance incident demonstrated this vector's effectiveness, with attackers modifying nameserver records at the registrar level. CDN poisoning injects malicious code into content delivery networks, compromising multiple sites simultaneously. Supply chain attacks target upstream dependencies, with the 2025 NPM incident affecting packages with 2 billion weekly downloads. Other attack vectors include social engineering vulnerabilities at domain registrars, as seen with the Convex hack.
Survey data confirms user awareness of these threats. Among respondents to our survey, 88% identify connecting to malicious sites as their primary concern, compared to 77% citing smart contract vulnerabilities. These results show that the market recognizes that frontend attacks are a significant threat vector.
Infrastructure Concentration Risk
Current DeFi frontend delivery exhibits centralization. Protocol interviews with multiple DeFi teams, that requested to remain anonymous, reveal preference for Vercel deployment for primary hosting. This concentration creates risks, as compromise of major hosting providers could simultaneously affect multiple protocols.
Although the protocols interviewed for this report displayed strong security practices overall, there is always room for improvement. The gap between compromise detection and user protection, combined with automated draining bot capabilities, creates critical exposure windows measured in minutes rather than hours. As attacks become more sophisticated and the number of vectors proliferates with the rise of generative AI, protocols will need to iteratively improve their frontend security over time.
Survey Demographics and User Composition
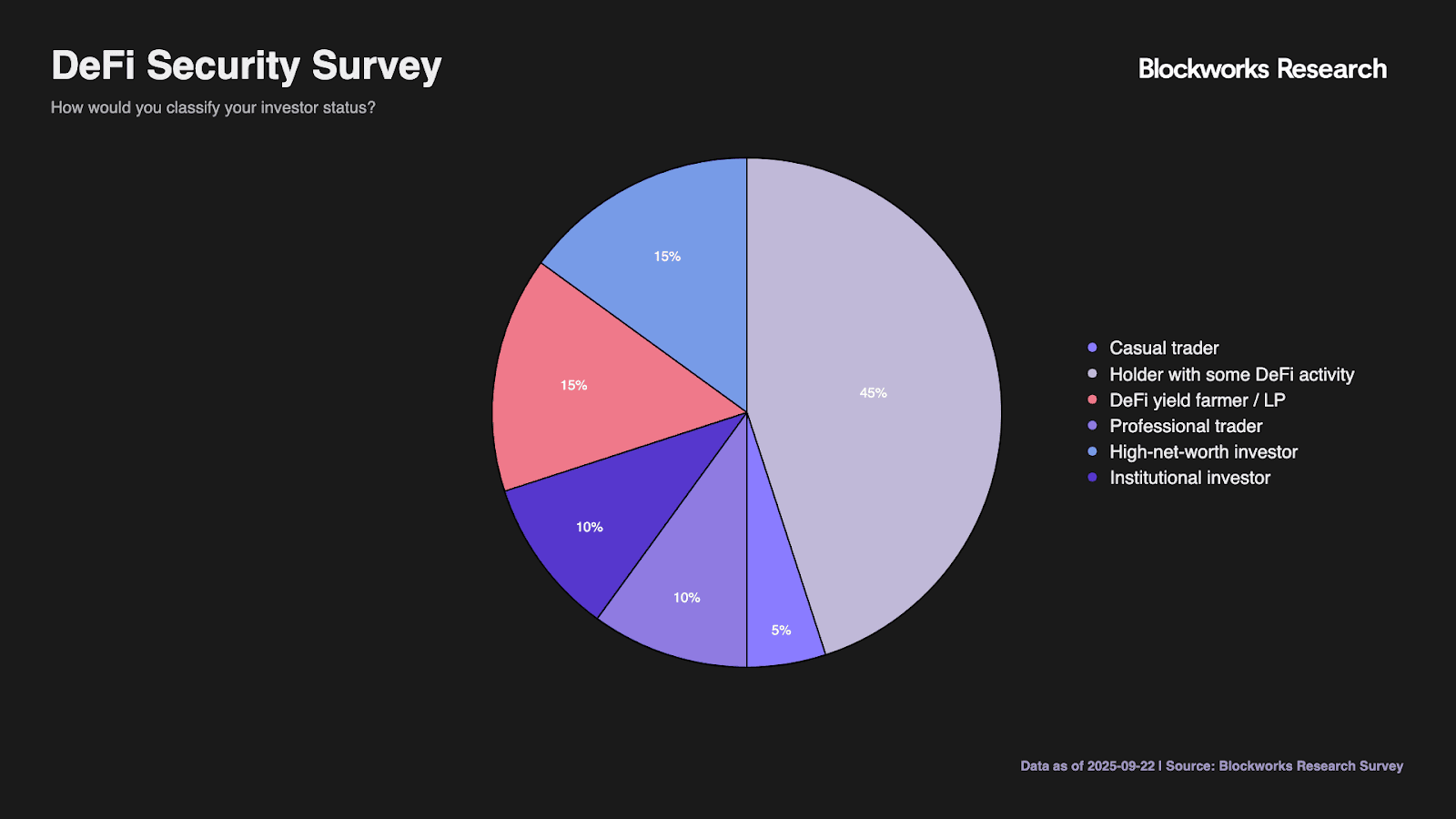
The survey captured a representative cross-section of the DeFi ecosystem, with 61% individual investors and traders forming the core respondent base. Protocol teams comprised 15% of responses, providing critical technical perspective, while finance professionals represented 20% of participants. The remaining investors were from venture capital, or were high networth individuals.
Investor classifications demonstrate a broad range of participation patterns. Long-term holders with DeFi activity represent 45% of respondents, indicating passive investors increasingly engage with DeFi beyond simple holding strategies. Professional traders and DeFi yield farmers each constitute 15% of the sample, while institutional investors managing external capital account for 10%.
User Security Behaviors
Access Patterns and Protection Measures
DeFi interaction frequency demonstrates active ecosystem engagement, with 30% accessing protocols daily and 60% weekly. This high-frequency usage creates repeated exposure to frontend risks, amplifying the importance of security measures.
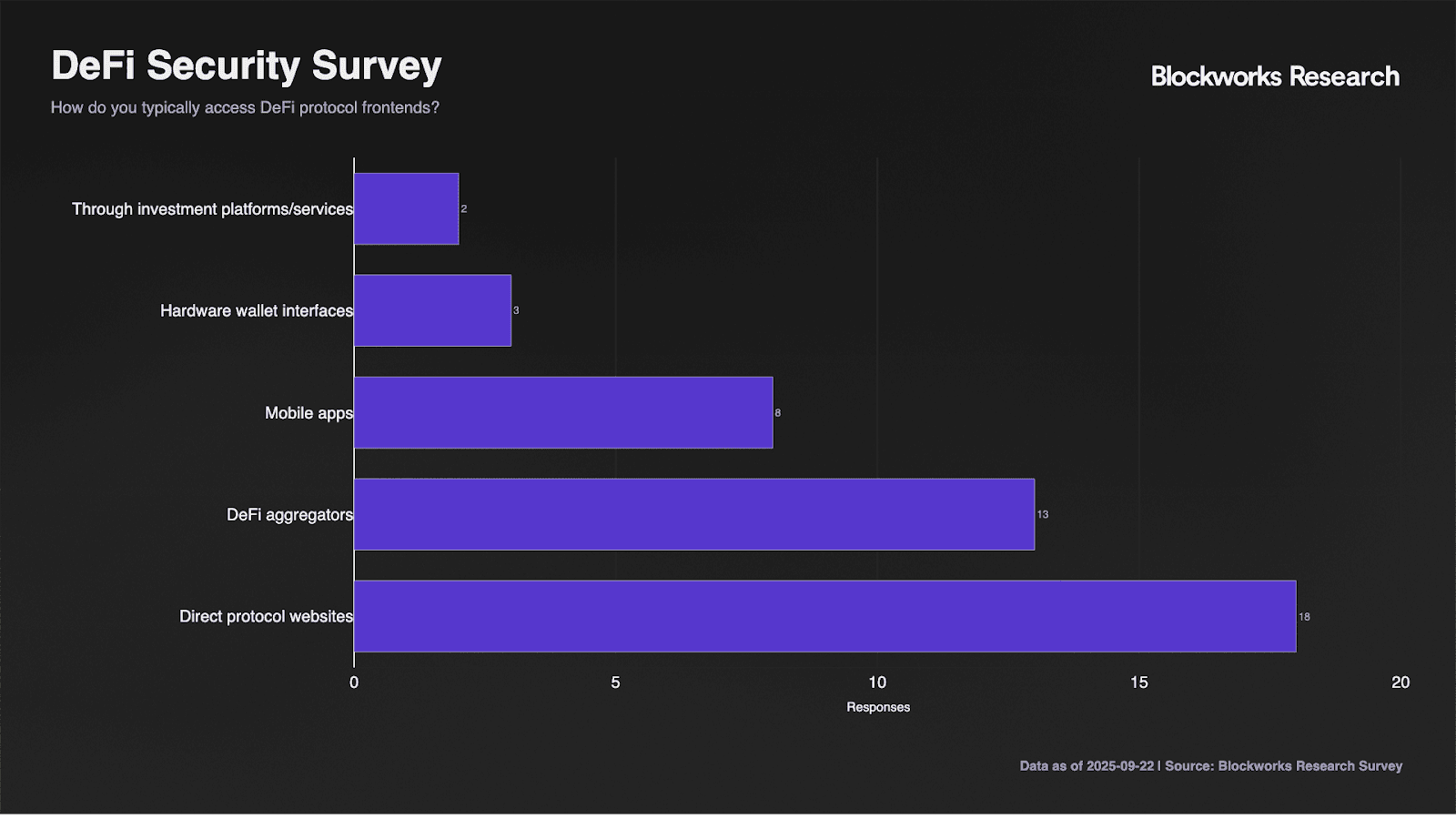
Direct access via official protocol frontend websites remains the dominant method of access at 90% adoption, though 65% also utilize DeFi aggregators for cross-protocol interactions. Mobile app usage at 40% indicates significant non-desktop exposure, while only 15% report access through hardware wallet interfaces.
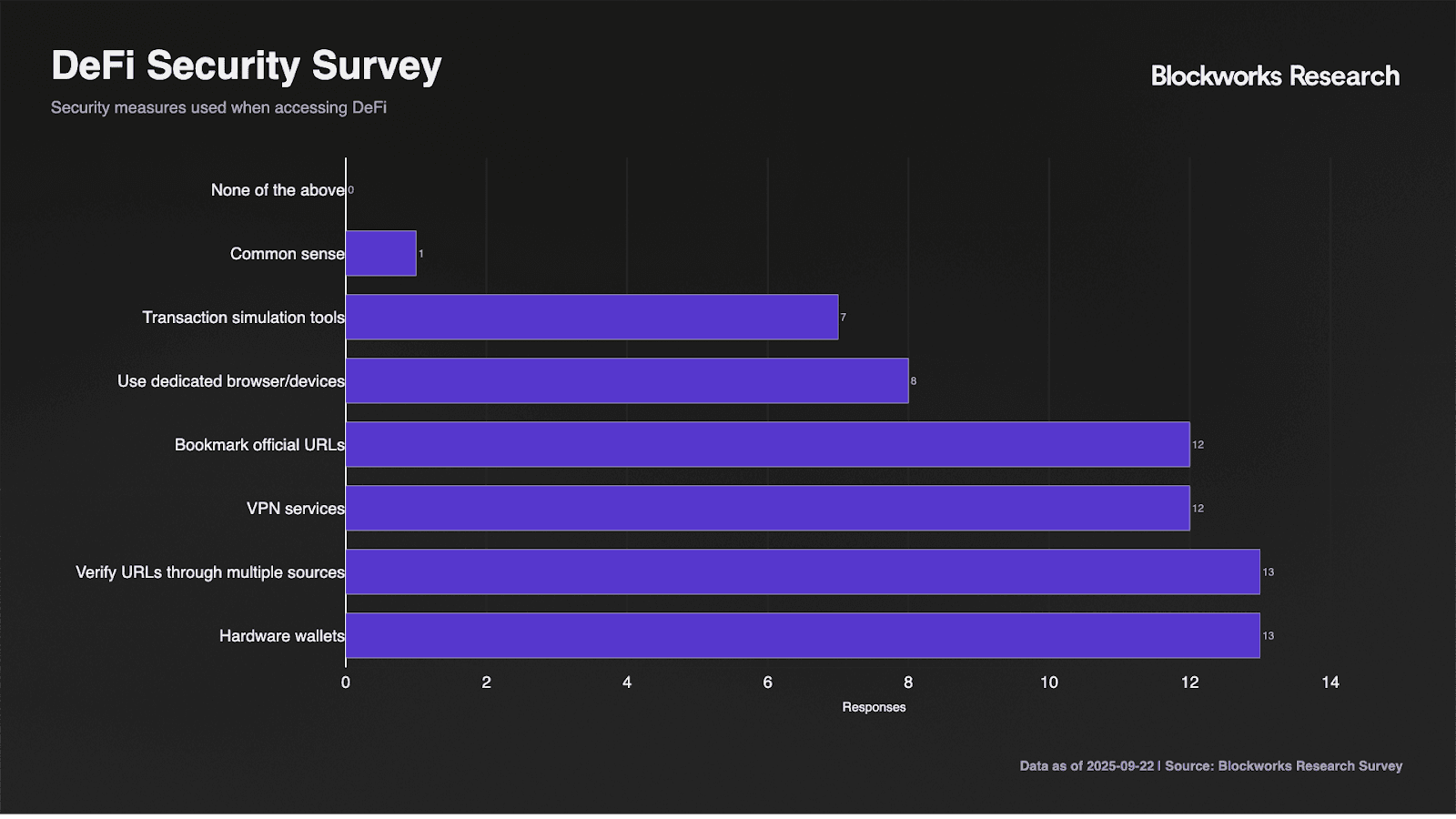
Security measure adoption reveals a cascade from passive to active protection. Hardware wallets achieve 65% penetration, marginally below the 71% who verify URLs through multiple sources. VPN services and bookmarked URLs both reach 60% adoption, representing baseline operational security. However, active protection measures show significant drop-off, with dedicated browser usage at 40% and transaction simulation tools at only 35%. This pattern indicates users readily adopt set-and-forget security but resist measures requiring ongoing engagement.
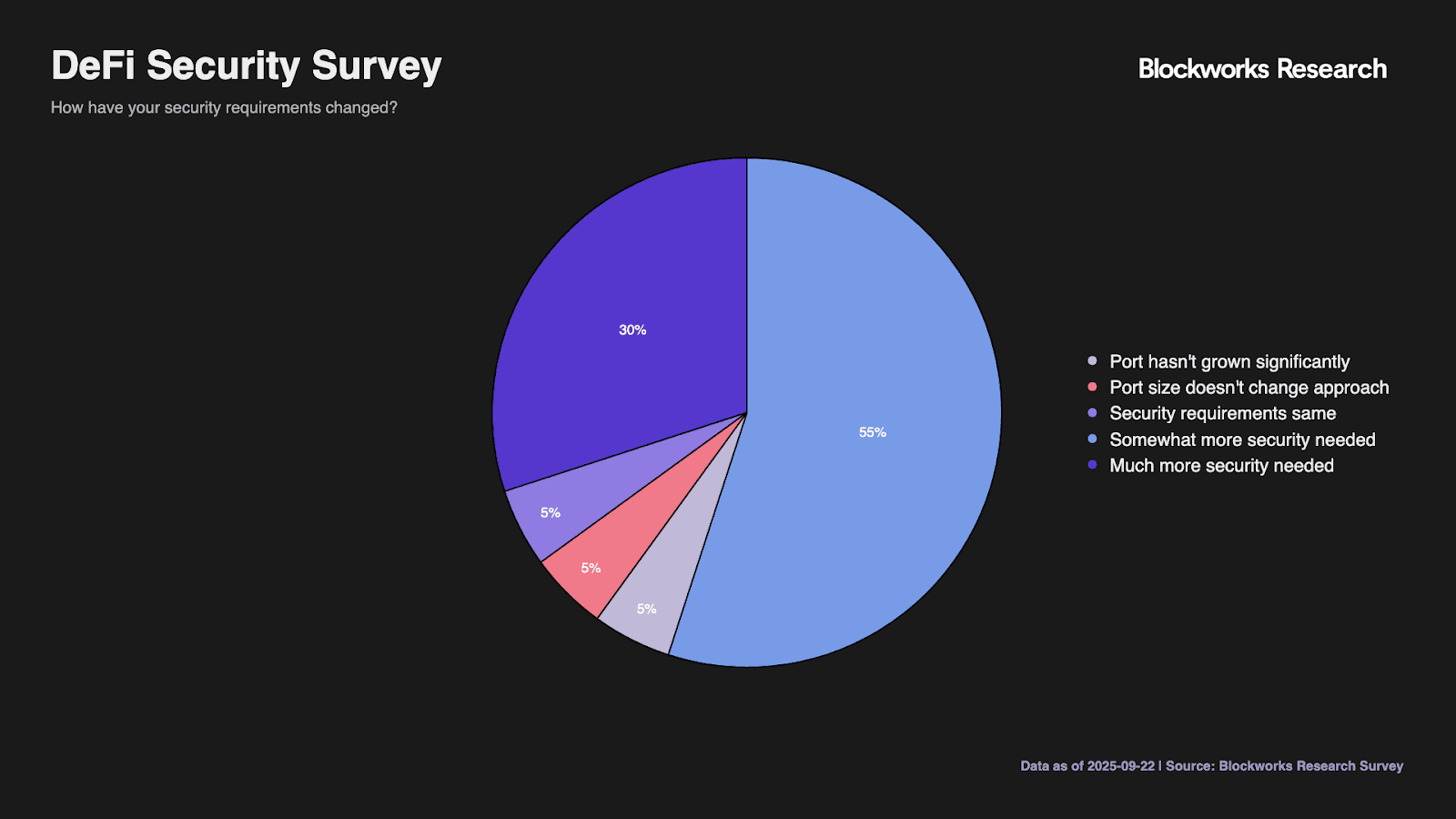
Portfolio growth correlates with evolving security practices, though implementation gaps persist. Among respondents, 30% report much more stringent security requirements as portfolios expanded, with 55% indicating somewhat increased stringency. Yet only 5% maintain static security regardless of portfolio size, suggesting near-universal recognition that larger holdings require enhanced protection.
Confidence and Incident Exposure
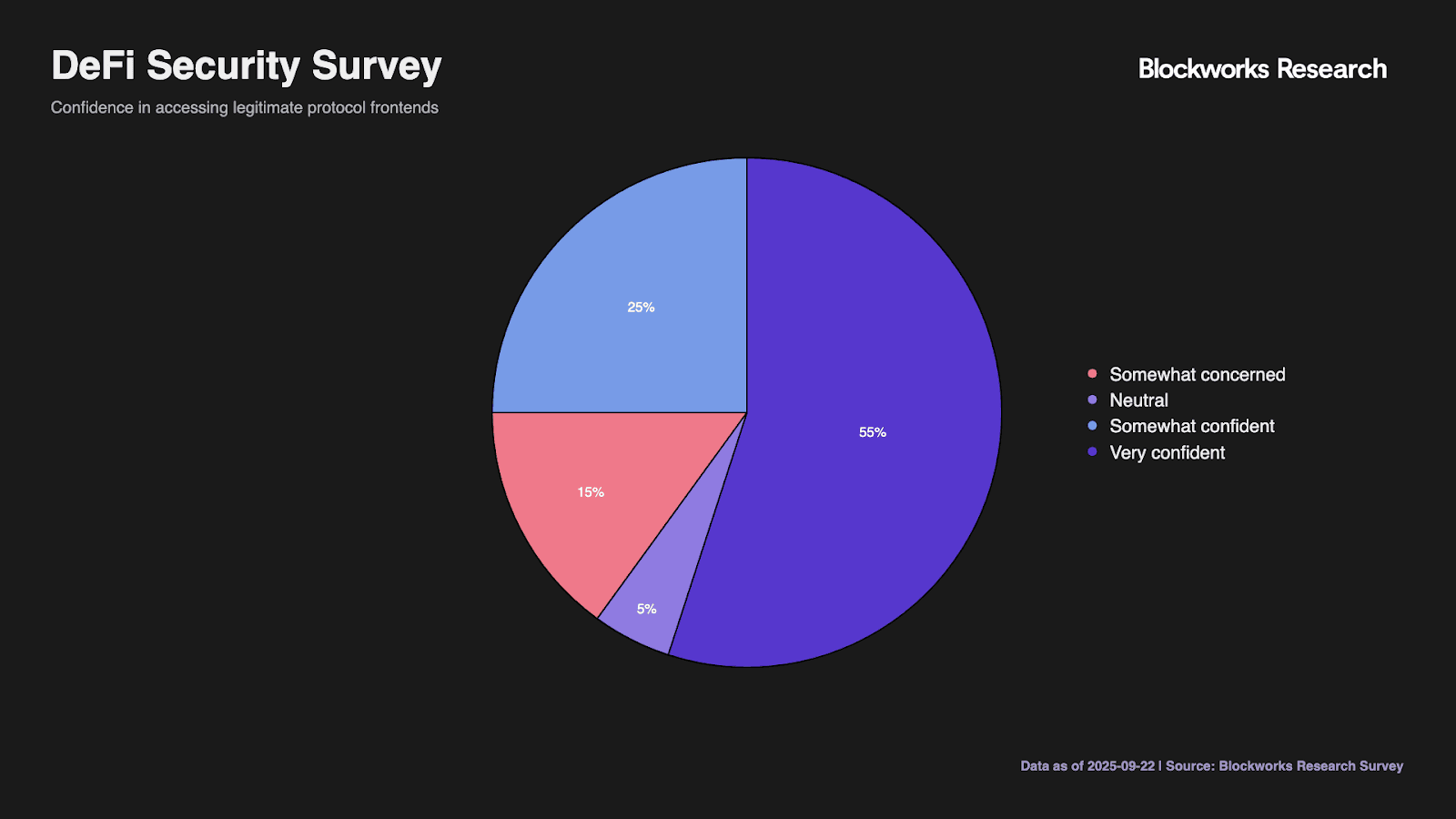
User confidence in identifying legitimate frontends reveals concerning overconfidence patterns. While 55% express very confident assessment abilities and 25% indicate somewhat confident, this self-assessment contrasts with actual incident rates. The 15% acknowledging concern about their identification capabilities likely represents more realistic self-assessment given the sophistication of modern phishing attempts.
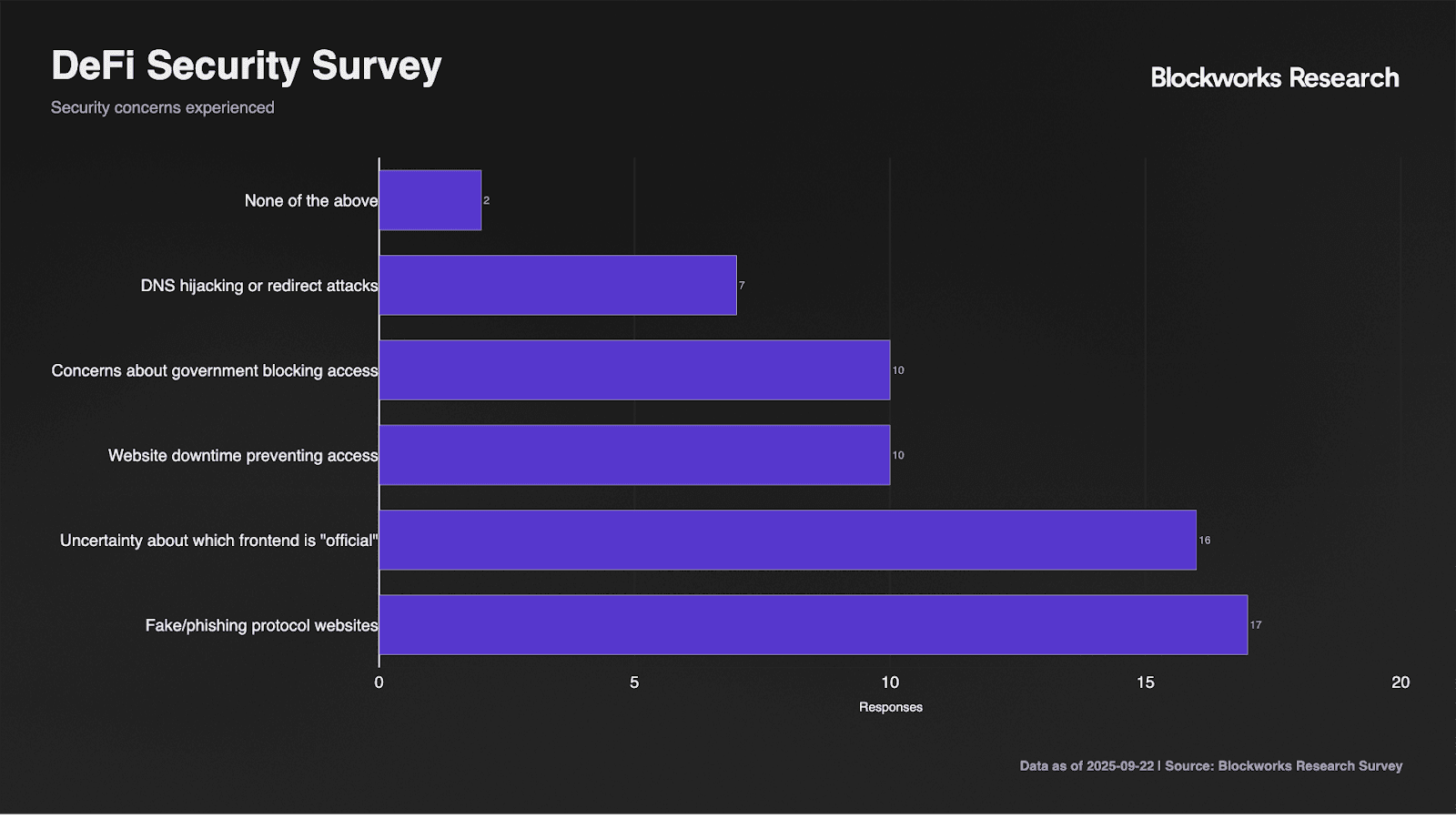
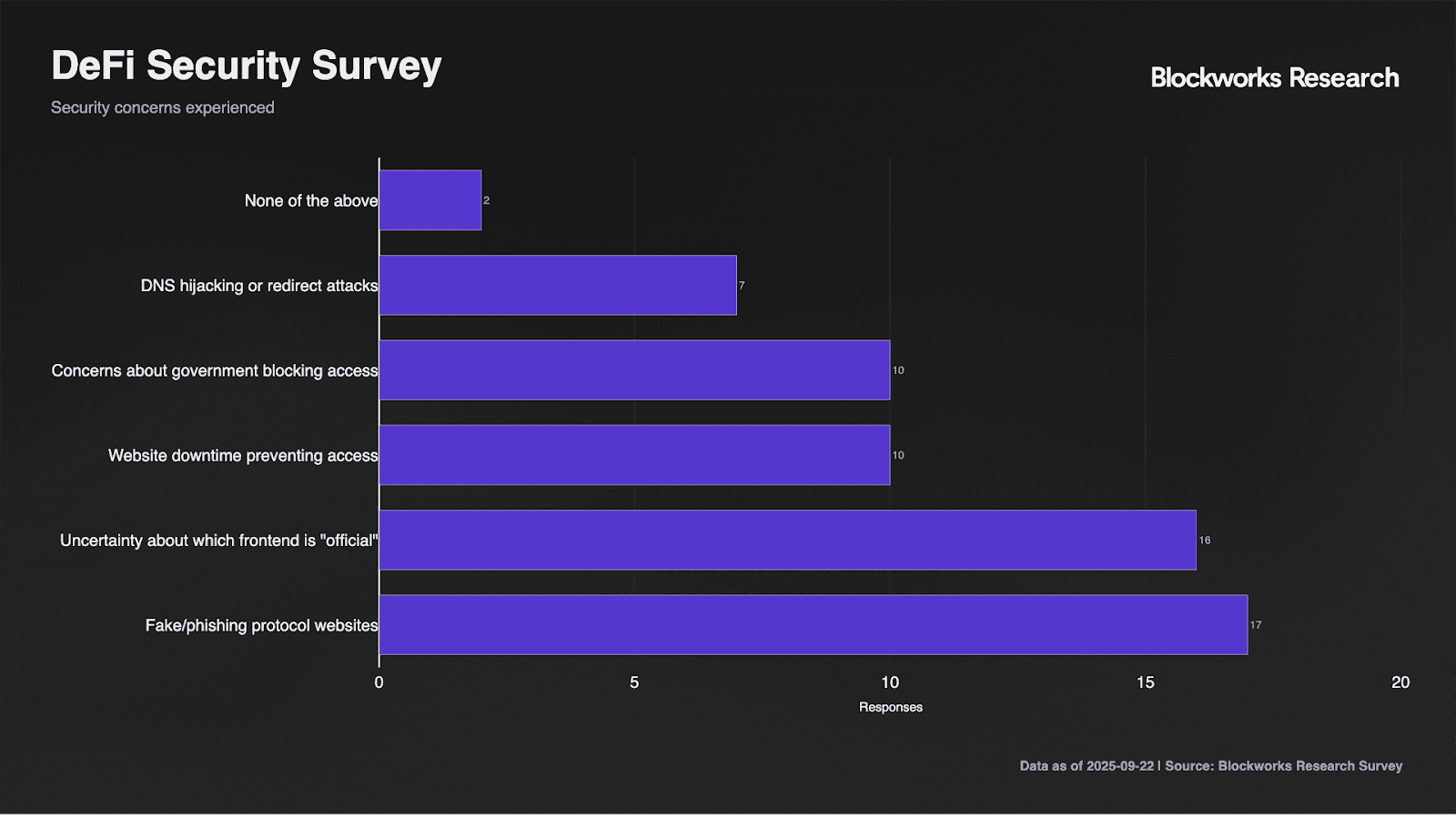
Survey responses highlight broad exposure to ecosystem vulnerabilities. Fake and phishing websites concern 85% of respondents, while 80% express uncertainty about which frontends are official. DNS hijacking concerns affect 35% of users, though this lower rate likely reflects limited technical understanding rather than reduced risk. Notably, 50% worry about government blocking and website downtime, indicating concerns extend beyond purely malicious attacks to include infrastructure reliability.
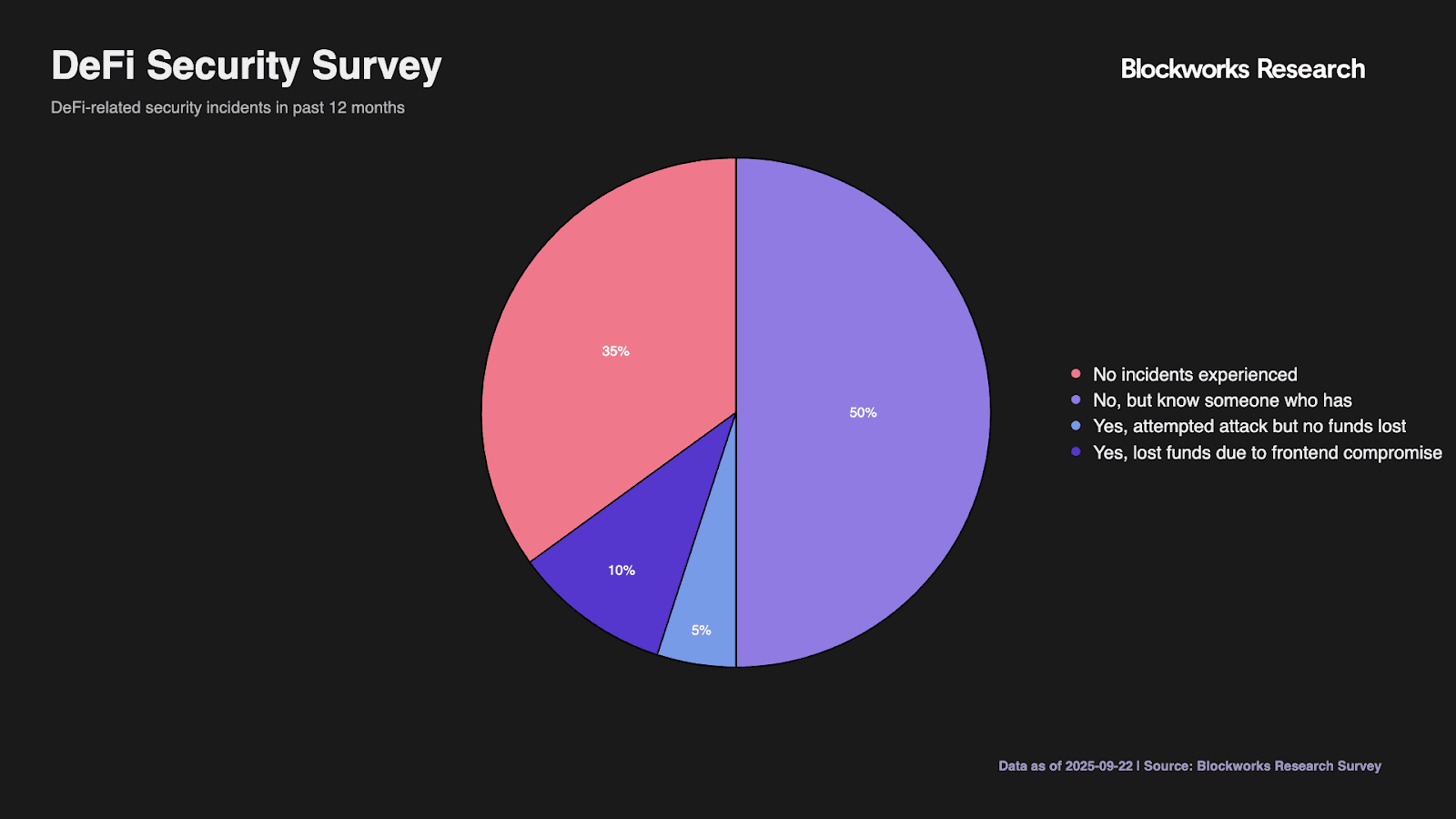
Direct incident exposure remains relatively contained at 10% experiencing fund losses and 5% encountering attempted attacks without losses. However, the 50% knowing affected individuals suggests broader reputational impact, while 35% reporting no incident awareness likely underestimates exposure given detection challenges. One respondent's open-text comment about security tools potentially adding "new risk vectors" highlights sophisticated understanding of security trade-offs.
Market Demand for a Security Solution
Risk Prioritization and Activity Impact
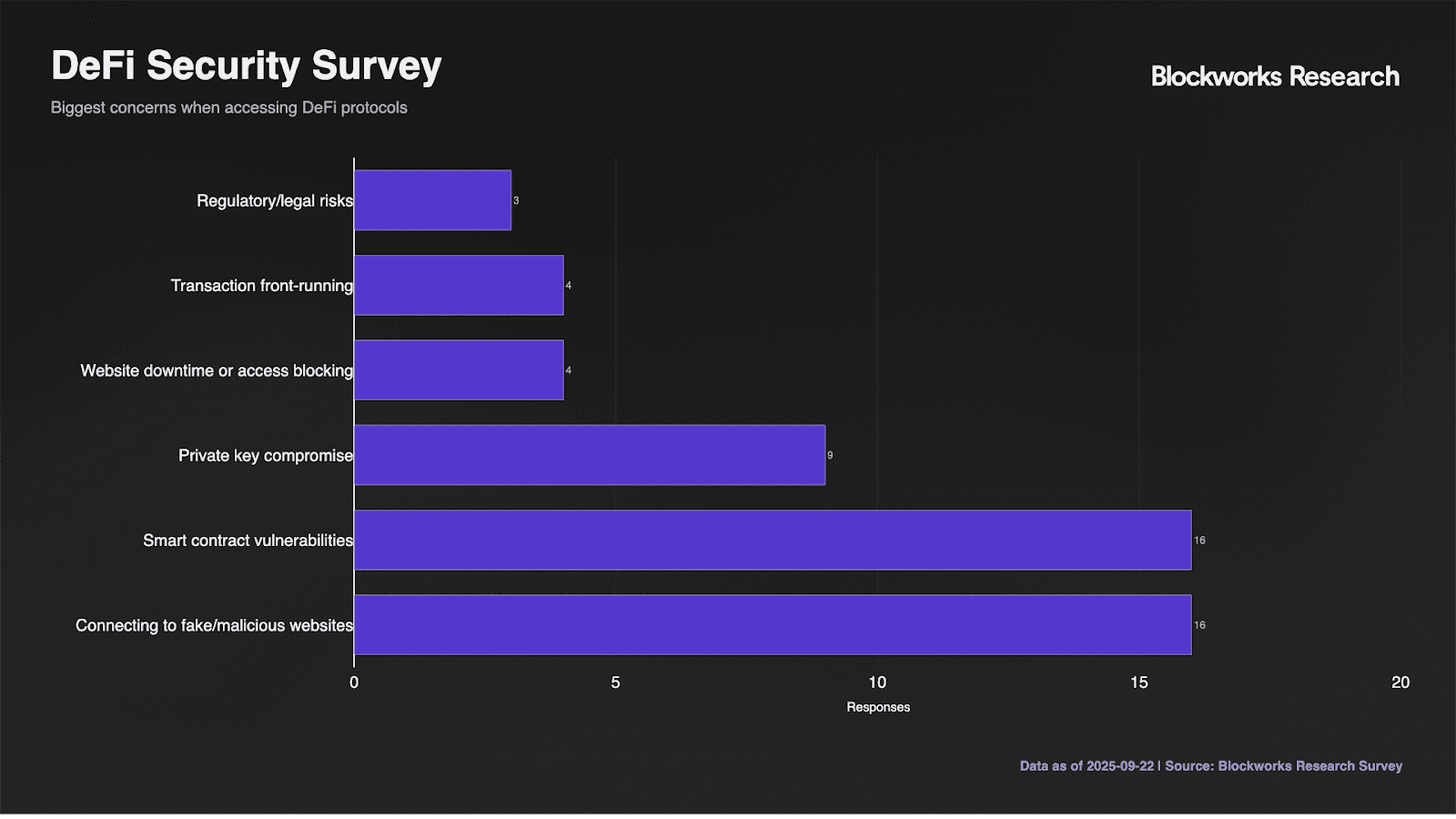
When forced to identify top concerns, respondents reveal nuanced risk assessment. Connecting to malicious websites and smart contract vulnerabilities tie at 80% each, indicating users view frontend and backend risks as equally threatening. Private key compromise concerns 45% of respondents, while regulatory risks worry only 15%. The 20% concerned about website downtime and transaction front-running suggests operational risks receive less attention than security threats.
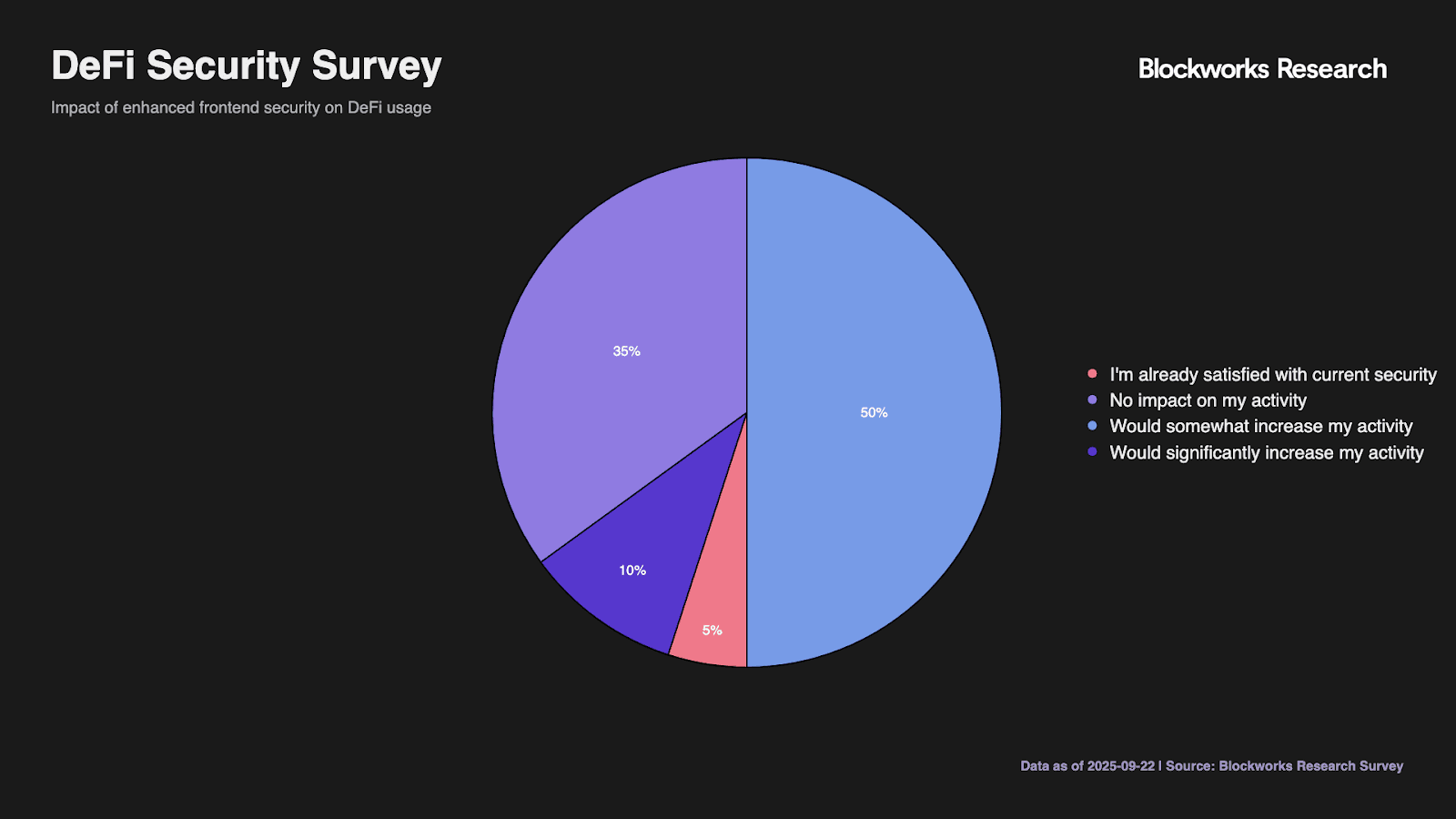
Enhanced frontend security would materially impact ecosystem participation. While 10% indicate security improvements would significantly increase their DeFi activity, the 50% reporting somewhat increased activity represents substantial latent demand. The 35% expecting no impact and 5% already satisfied with current security suggest a ceiling on security-driven growth. Notably, zero respondents dismiss frontend security as unimportant, confirming universal recognition of the issue.
Verification Solution Demand
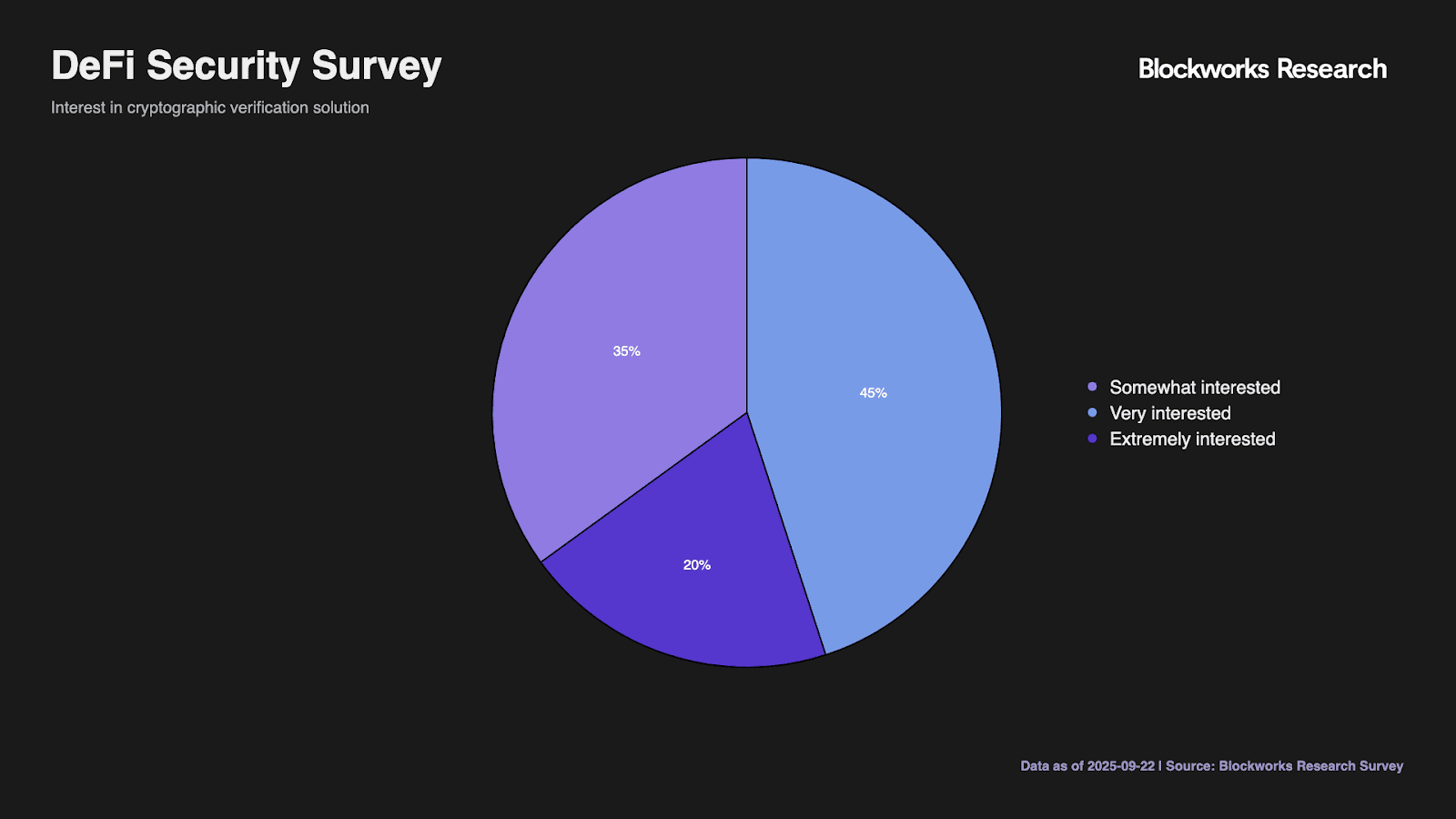
Interest in cryptographically verified frontends shows remarkable consistency, with 20% extremely interested in immediate adoption and 35% very interested in likely adoption. The 45% somewhat interested category likely includes price-sensitive users awaiting market validation. The complete absence of disinterest confirms product-market fit for verification solutions.
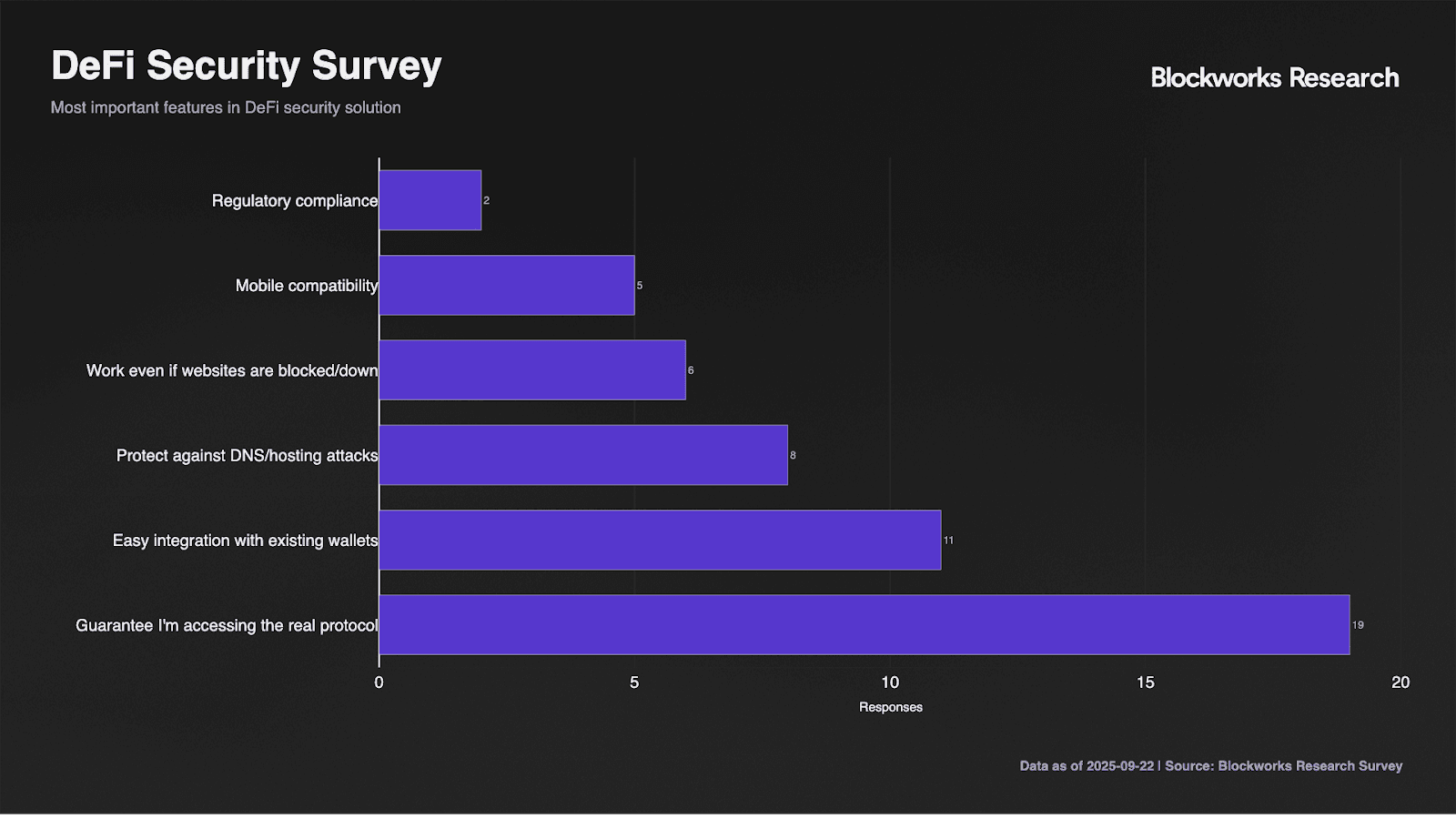
Feature prioritization crystallizes user requirements. The 95% demanding guaranteed authentic protocol access dwarfs all other considerations, establishing this as the minimum viable product requirement. Easy wallet integration at 55% suggests users expect security within existing workflows rather than separate applications. DNS protection interests 40% of respondents, while only 30% prioritize resilience during downtime. Mobile compatibility at 25% and regulatory compliance at 10% rank lowest, though mobile's importance likely increases as that access method grows.
Adoption Patterns and Information Flow
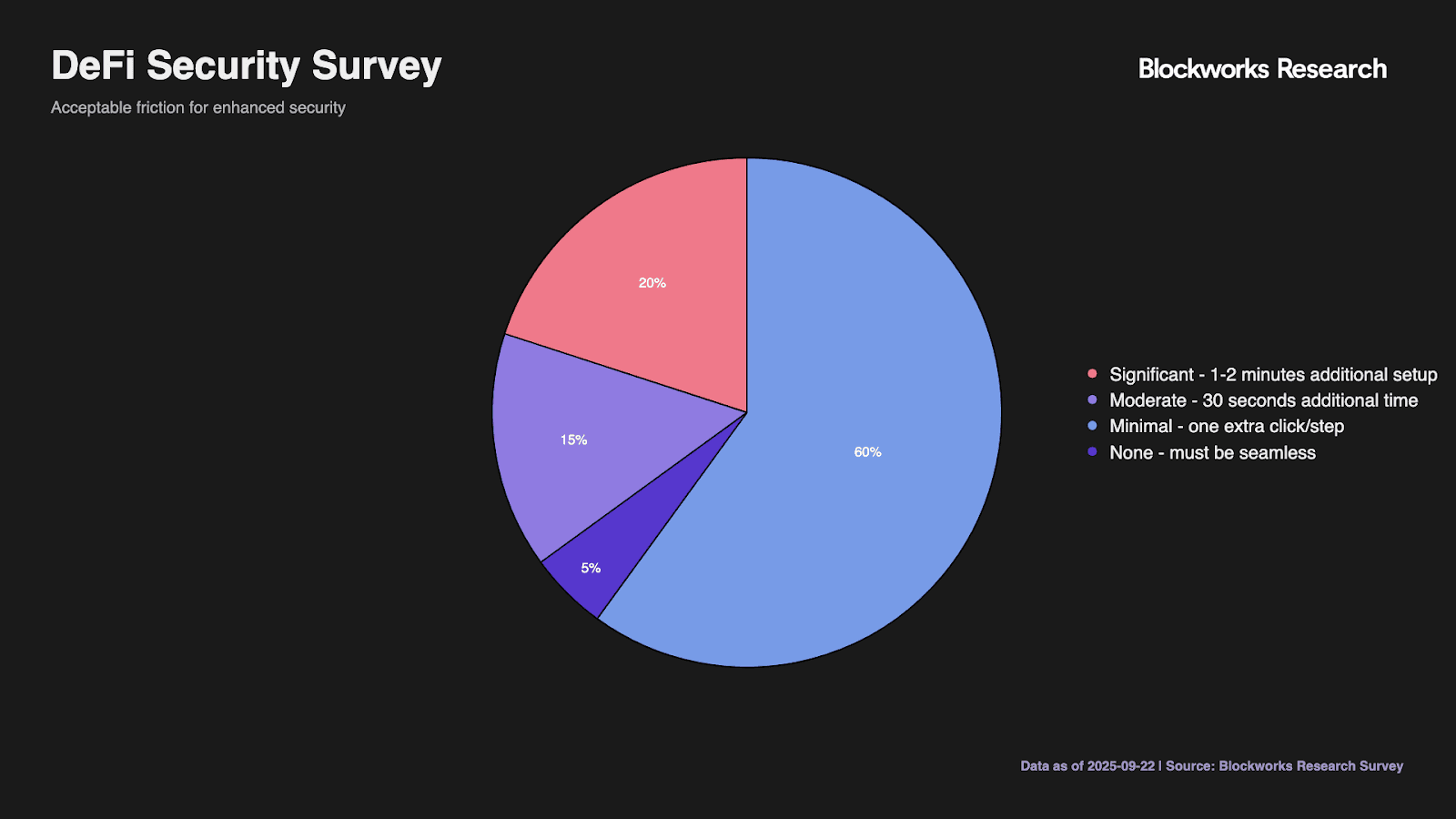
Friction tolerance data reveals the critical implementation constraint. Only 5% demand completely seamless integration, likely representing the most valuable but demanding users. The 60% accepting minimal friction of one extra click or step defines the viable implementation window. Another 15% tolerate 30-second delays, while 20% accept 1-2 minute setup processes. Notably, zero respondents selected "whatever it takes for security," confirming that even security-conscious users maintain usability requirements.
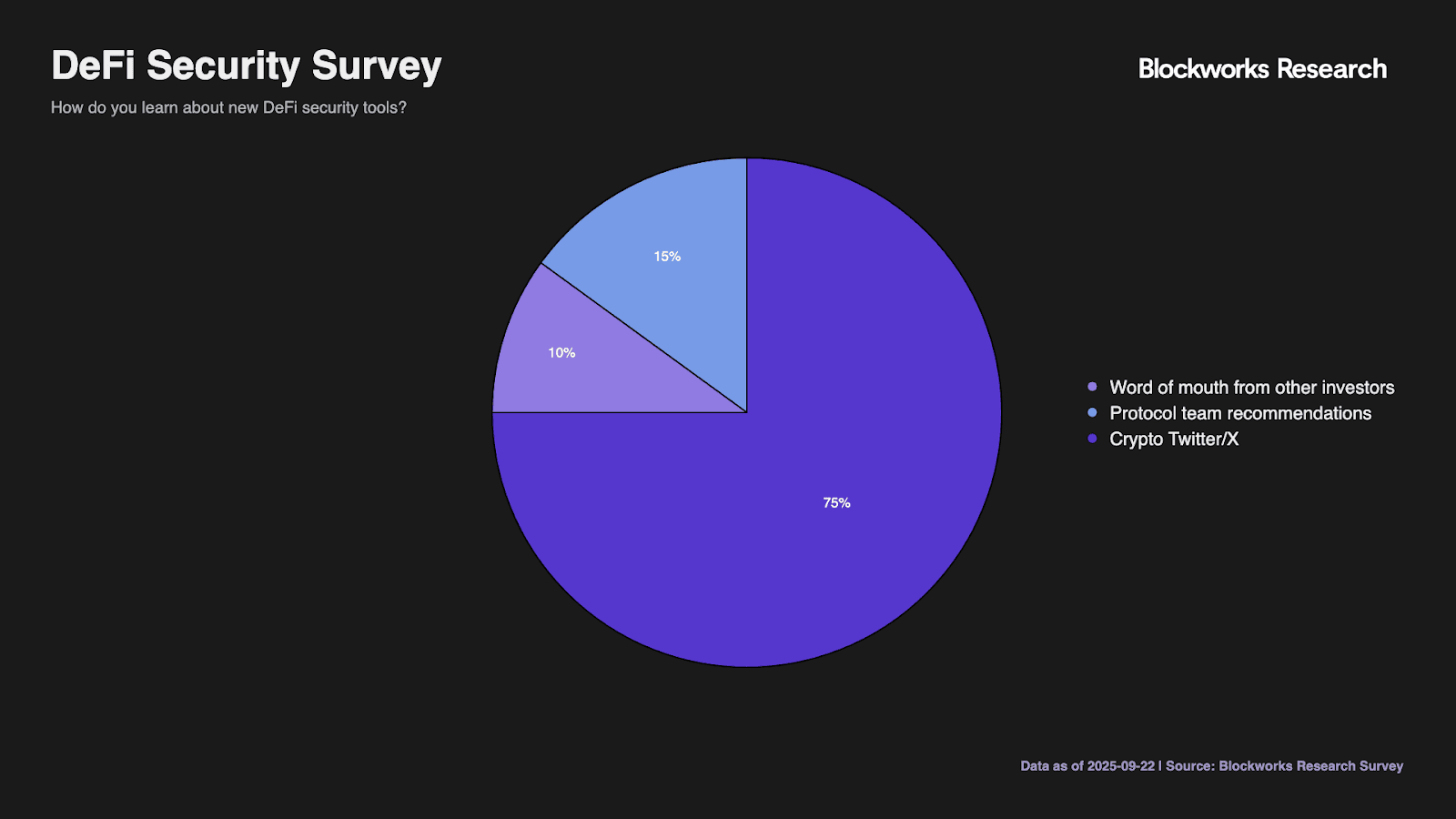
Information discovery patterns highlight marketing channel importance. Crypto Twitter dominates at 75%, confirming its role as the primary information vector in DeFi. Protocol team recommendations influence 15% of users, while word of mouth affects 10%.
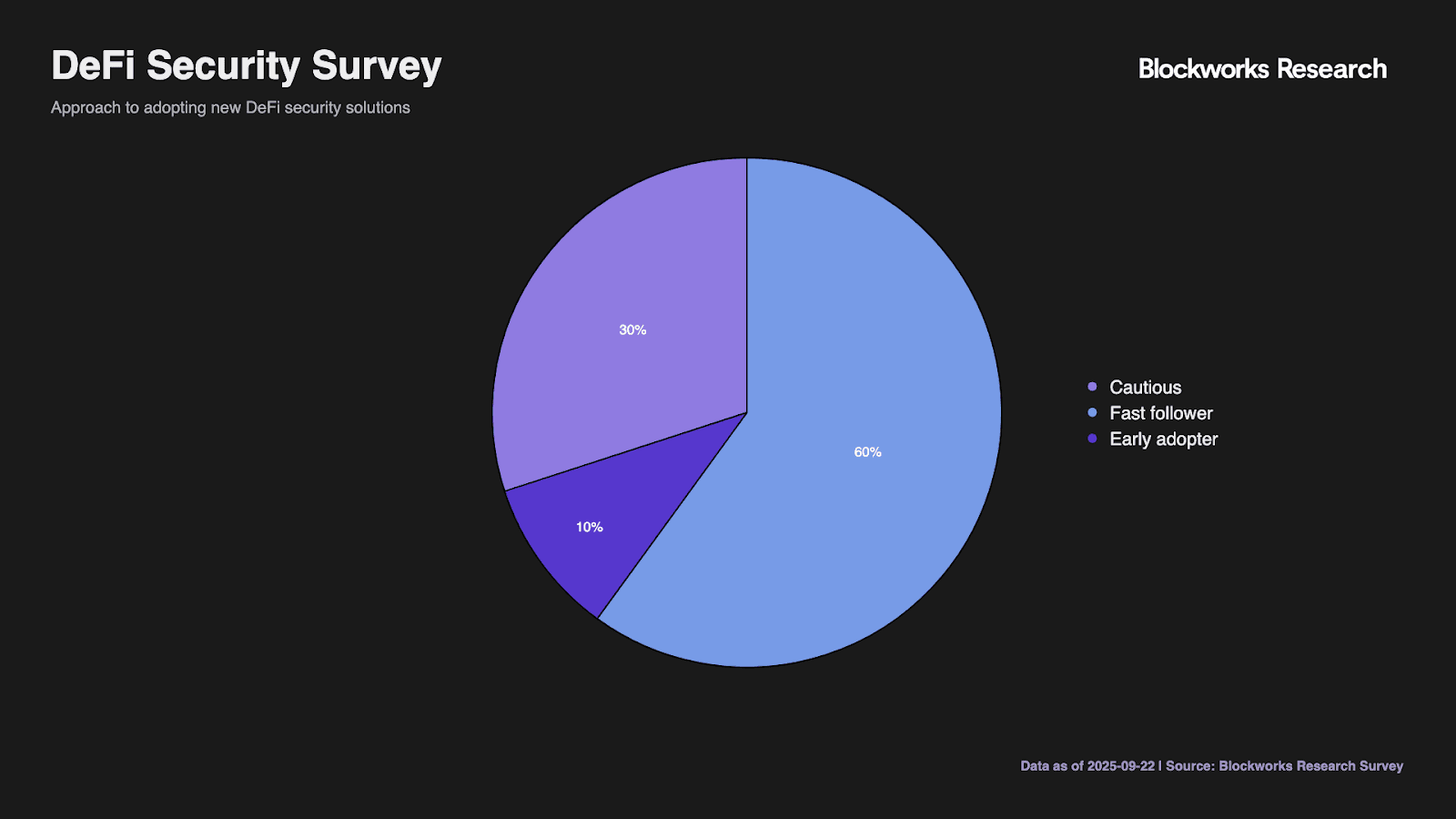
Security solution adoption approaches reveal a cautiously optimistic market. Early adopters willing to try new tools immediately constitute only 10%, providing a limited initial market. However, 60% identify as fast followers who adopt after seeing success, creating momentum potential. The 30% requiring broad adoption and proven track records represent the mainstream market.
Protocol Security Practices
Development teams employ varied security measures without ecosystem standardization, though common practices are emerging across leading protocols. All interviewed teams implement cryptographically signed commits using hardware keys, with specific approaches ranging from one team requiring "YubiKeys for all commits with reproducible Next.js builds" to another "working on reproducible builds for TEEs."
CI/CD Pipeline Hardening and Content Integrity
Protocol teams have implemented comprehensive CI/CD security frameworks beyond basic code signing. Protected GitHub branches requiring signed commits and mandatory peer reviews represent universal baseline practices, with teams enforcing "SSO + 2FA for all commits" and implementing dev/staging/prod environment workflows. Content integrity measures include pinned dependencies, build hashes, and strict Content Security Policy headers with allowlists, while Vercel Enterprise provides "encrypted secrets and automated security scanning" alongside automated Dependabot and npm audit processes running as GitHub Actions.
Teams supplement automated tooling with active security testing, including blackbox penetration testing, though approaches vary significantly. One protocol noted their primary security incident initially appeared to be "a supply chain incident that was secretly overwriting instructions" but ultimately traced to "a totally bungled release by a wallet's WalletConnect integration," highlighting the complexity of diagnosing frontend vulnerabilities in the interconnected DeFi ecosystem.
Hosting Infrastructure and Backup Strategies
Despite philosophical alignment with decentralization, practical deployment reality reveals a strong Vercel dependence for primary hosting across all interviewed protocols. Teams acknowledge this concentration risk, with one explicitly stating plans to "move away from Vercel mostly for security reasons," though migration timelines remain indefinite. Current risk mitigation includes Cloudflare DNS with DDoS protection and "pretty locked down" transfer restrictions to prevent social engineering attacks on DNS services.
Backup strategies vary in sophistication and automation. While some teams maintain "separate backup vanilla functionality frontends deployed with password protection," others rely primarily on monitoring "through multiple vendors" with manual intervention processes. The gap between compromise detection and response creates critical exposure windows, with teams acknowledging that backup plans "don't help if core Web3 packages we rely on are compromised."
User Communication and Education Gaps
Official frontend URL communication relies heavily on Web2 social media platforms, with teams primarily using "Twitter, Discord, etc." and verified social media accounts to establish legitimacy. Despite frontend attacks representing users' primary security concern, protocol teams provide minimal user education, with responses ranging from "not much aside from mentioning in spots to watch out for leaking private keys" to basic documentation sites covering frontend and backend security.
This education gap reflects broader industry challenges, as teams report user feedback focused on UX concerns rather than security awareness. One team noted users "want fast communications any time something happens" and prefer "more static decentralized domains that are verifiable and not getting frequent/experimental updates," indicating user preference for stability over cutting-edge features that might introduce additional attack vectors.
Key Trends and Solutions: Radworks Addressing Frontend Vulnerabilities
The survey reveals a mature market recognizing frontend vulnerabilities yet struggling with implementation barriers. The 88% identifying frontend attacks as primary concern, contrasted with only 41% using transaction simulation tools, establishes clear demand for accessible security infrastructure. This protection gap creates natural alignment with decentralized verification solutions.
Radworks' technical architecture directly addresses the vulnerabilities concerning 88% of respondents. Radicle's Heartwood protocol, the peer-to-peer code collaboration stack funded by the Radworks ecosystem, features peer-to-peer distribution that ensures content availability even during coordinated attacks, addressing the DNS hijacking fears.
Radworks' git-based architecture maintains familiar developer workflows while adding security layers, potentially meeting the minimal friction requirement. The planned Radworks App providing a local-first launcher for decentralized frontends could operate within the one-click tolerance threshold, while browser extension development could achieve near-seamless integration for users demanding no friction.
The convergence of technical capability and market timing creates favorable conditions. Recent incidents like the npm incident establish urgency, while regulatory evolution toward operational resilience requirements creates institutional demand for verifiable infrastructure. Radworks' Swiss non-profit structure provides regulatory clarity while maintaining decentralized governance, appealing to institutions navigating compliance requirements.
Risk Assessment
Although there is clear demand for decentralized frontend solutions, challenges remain. The survey data revealing only 41% transaction simulation tool usage despite 88% security awareness indicates a fundamental behavioral gap—users intellectually recognize risks but resist operational changes disrupting established workflows. This extends to the paradox of Web3 developers overwhelmingly using GitHub despite philosophical alignment with decentralization, suggesting convenience consistently outweighs ideology in technology adoption decisions.
The 59% of users accepting only minimal friction creates a design constraint for decentralized solutions, which inherently require additional verification steps, key management, and node discovery mechanisms absent in centralized platforms. Furthermore, the concentration of frontend attacks creates a prisoner's dilemma where individual protocols benefit from enhanced security but lack incentive to bear switching costs unless competitors move simultaneously, perpetuating ecosystem-wide vulnerability despite available solutions.
Product execution and adoption barriers present immediate challenges to market penetration. Radicle faces GitHub's effective monopoly with 56 million users versus Radicle's ~2,000 repositories. Network effects work against challengers as developers collaborate where their peers are active, creating self-reinforcing centralization even among Web3 teams philosophically aligned with decentralization.
Conclusion
The DeFi frontend security landscape is at a turning point. Awareness of frontend vulnerabilities is widespread, yet adoption of protective measures lags, leaving the ecosystem exposed to systemic risk. At the same time, protocol teams acknowledge the risks of centralized hosting but face practical challenges in migrating to more resilient alternatives.
User behavior highlights the tension between security and usability: while participants recognize the importance of protection, friction sensitivity continues to limit adoption of advanced tools. This behavioral gap underscores the need for solutions that combine verifiable security with minimal disruption to established workflows.
Looking forward, market demand is poised to grow as institutional investors emphasize operational resilience, regulators move toward higher infrastructure standards, and high-profile exploits reinforce the urgency of stronger protections. Together, these forces suggest that security-focused infrastructure and tools that balance robustness with usability will play a defining role in shaping the next phase of DeFi adoption and maturity.
This research report has been funded by Radworks. By providing this disclosure, we aim to ensure that the research reported in this document is conducted with objectivity and transparency. Blockworks Research makes the following disclosures: 1) Research Funding: The research reported in this document has been funded by Radworks. The sponsor may have input on the content of the report, but Blockworks Research maintains editorial control over the final report to retain data accuracy and objectivity. All published reports by Blockworks Research are reviewed by internal independent parties to prevent bias. 2) Researchers submit financial conflict of interest (FCOI) disclosures on a monthly basis that are reviewed by appropriate internal parties. Readers are advised to conduct their own independent research and seek the advice of a qualified financial advisor before making any investment decisions.