This research report has been funded by Union.fi Labs. By providing this disclosure, we aim to ensure that the research reported in this document is conducted with objectivity and transparency. Blockworks Research makes the following disclosures: 1) Research Funding: The research reported in this document has been funded by Union.fi Labs. The sponsor may have input on the content of the report, but Blockworks Research maintains editorial control over the final report to retain data accuracy and objectivity. All published reports by Blockworks Research are reviewed by internal independent parties to prevent bias. 2) Researchers submit financial conflict of interest (FCOI) disclosures on a monthly basis that are reviewed by appropriate internal parties. Readers are advised to conduct their own independent research and seek advice of qualified financial advisor before making investment decisions.
The Cross‑Chain Interoperability Stack
Key Takeaways
- Interoperability is fragmenting into multiple design archetypes with each approach optimizing for different points on the security-UX-cost frontier.
- Modularity is winning as protocols with pluggable components adapt faster to new execution environments and regulatory constraints.
- Liquidity and capital efficiency drive adoption through native asset movement that eliminates fragmentation, while generalized messaging expands design space for omnichain dApps.
- Security assumptions are converging toward minimized trust through zero-knowledge proofs, optimistic dispute resolution, and permissionless validation networks.
Introduction
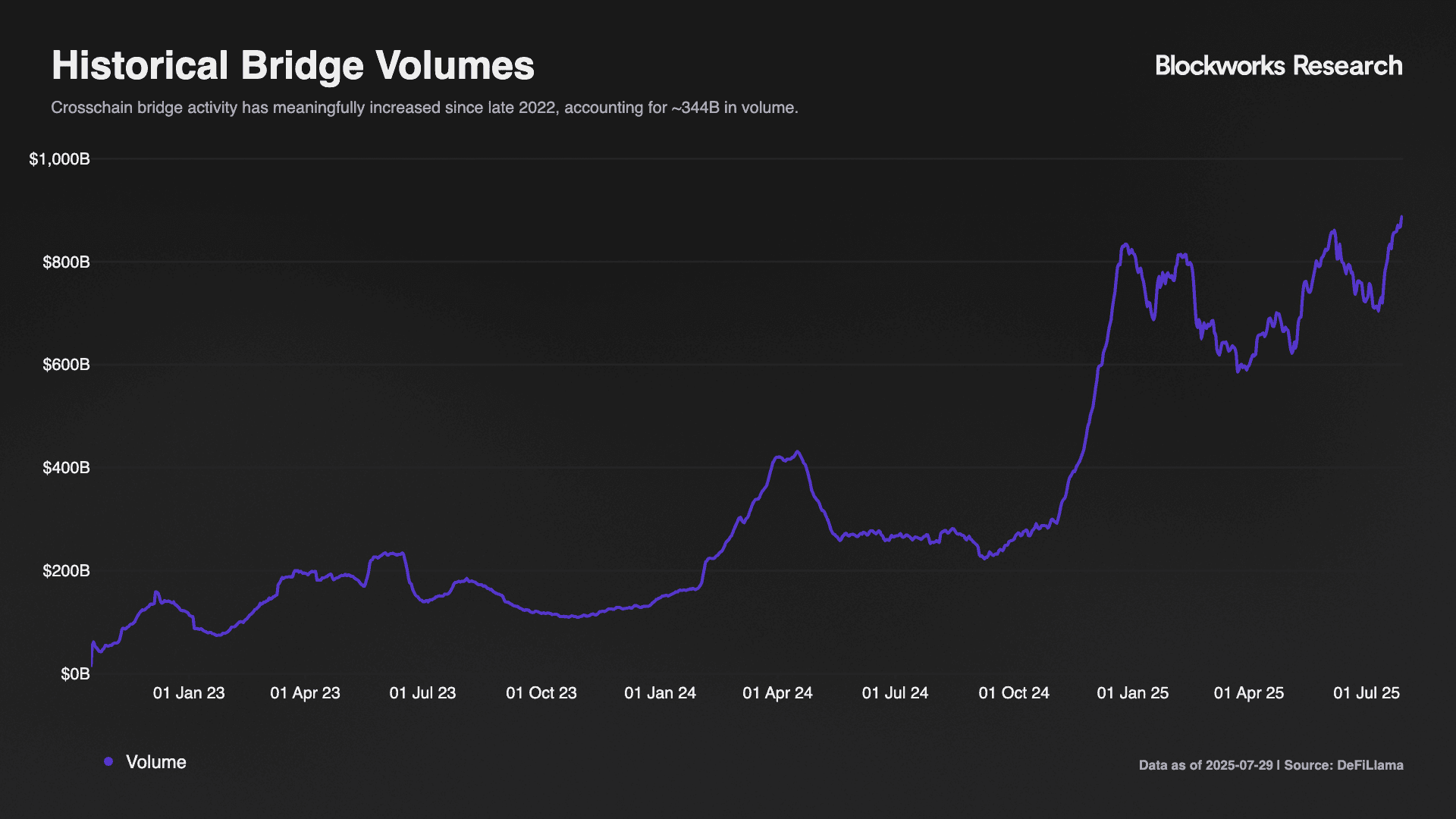
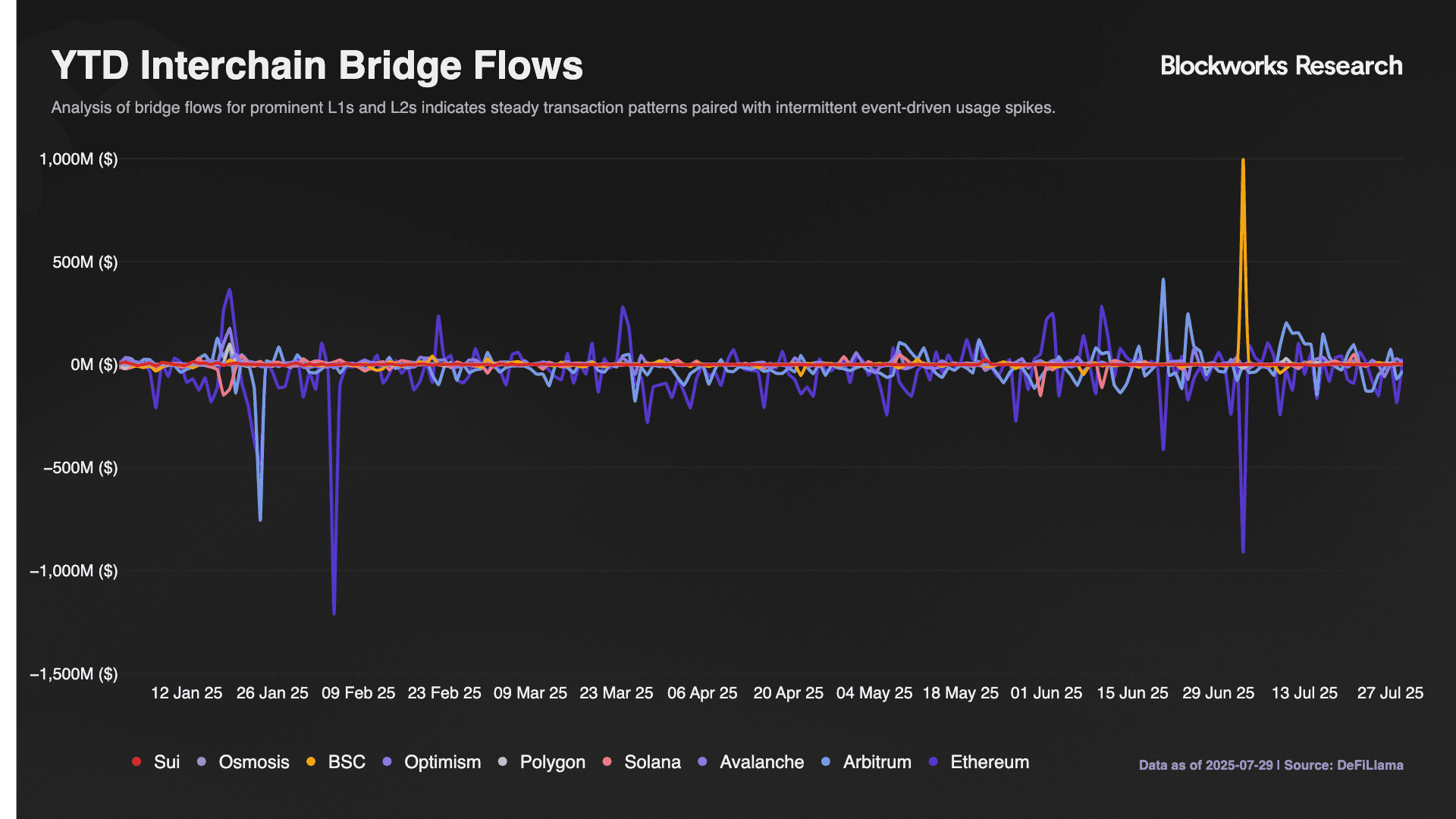
The march toward an interoperable and onchain-by-default internet depends on reliable messaging and value transfer across heterogeneous domains. Crosschain protocols now process >$1.3T in combined annual transfer volume and secure tens of millions of user interactions, yet no single design dominates. This fragmentation reflects fundamental trade-offs between trust assumptions, execution speed, and capital efficiency that each protocol addresses through distinct architectural choices.
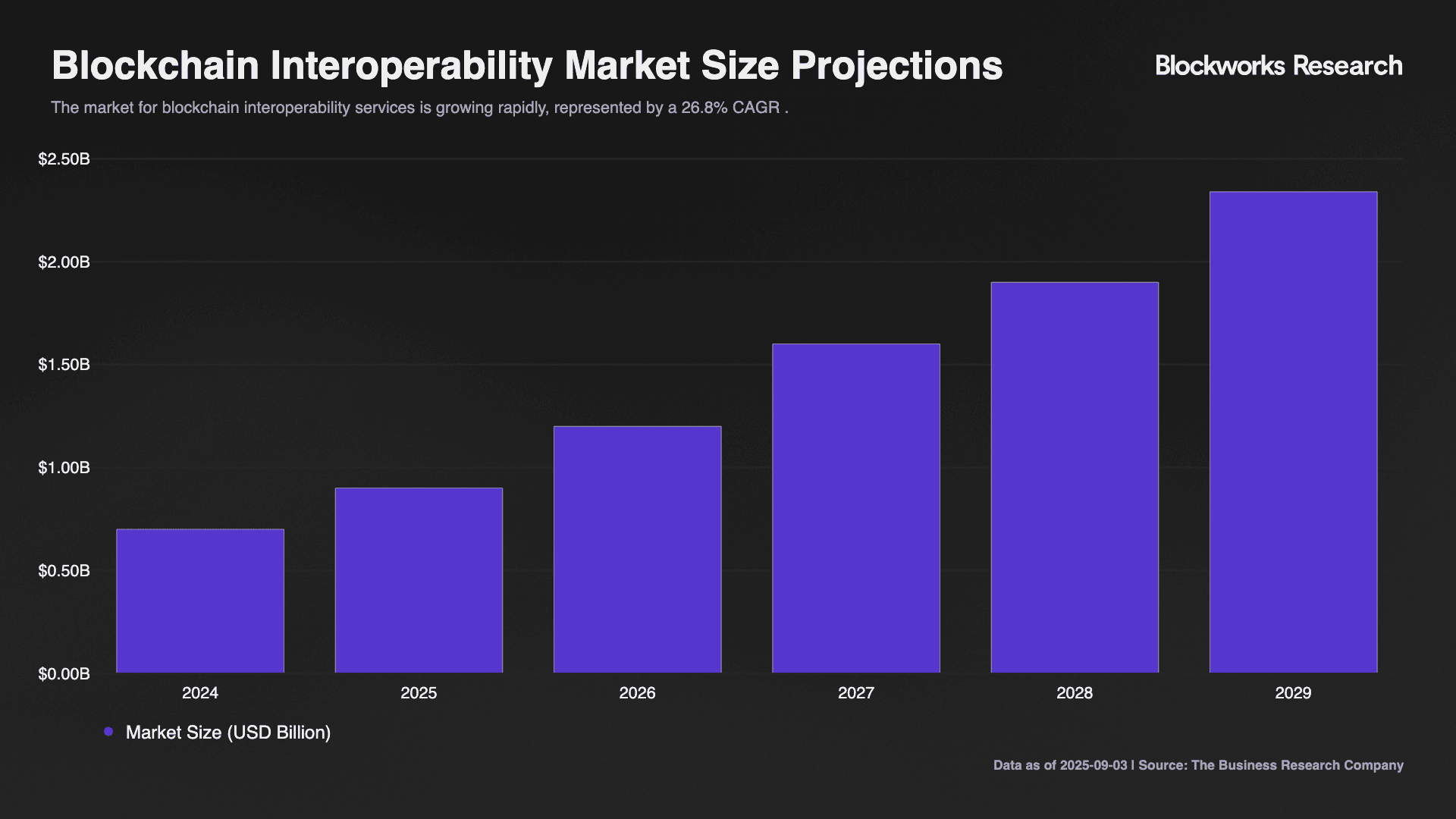
The blockchain interoperability services market is projected to expand from $0.7B in 2024 to $2.34B by 2029, representing a 26.8% CAGR in enterprise revenues that underscores the urgency of architectural decisions being made today. With 2025 expected to reach $0.9B in service provider revenues, the window for establishing dominant design patterns is narrowing as capital and developer mindshare consolidate around proven approaches.
Understanding these trade-offs is critical for builders, investors, and treasury strategists navigating an increasingly multichain landscape. Unlike previous generations of bridges that prioritized speed over security or liquidity over messaging flexibility, today's protocols are converging on modular designs that offer pluggable security models and programmable execution environments. Interoperability protocols are not merely competing for market share but defining distinct categories within the broader interoperability stack. Each addresses specific use cases, risk tolerances, and integration requirements that collectively enable the composable, multichain infrastructure layer underlying decentralized finance, gaming, and institutional adoption.
Architectural Deep‑Dive
LayerZero: Modular Security and Omnichain Messaging
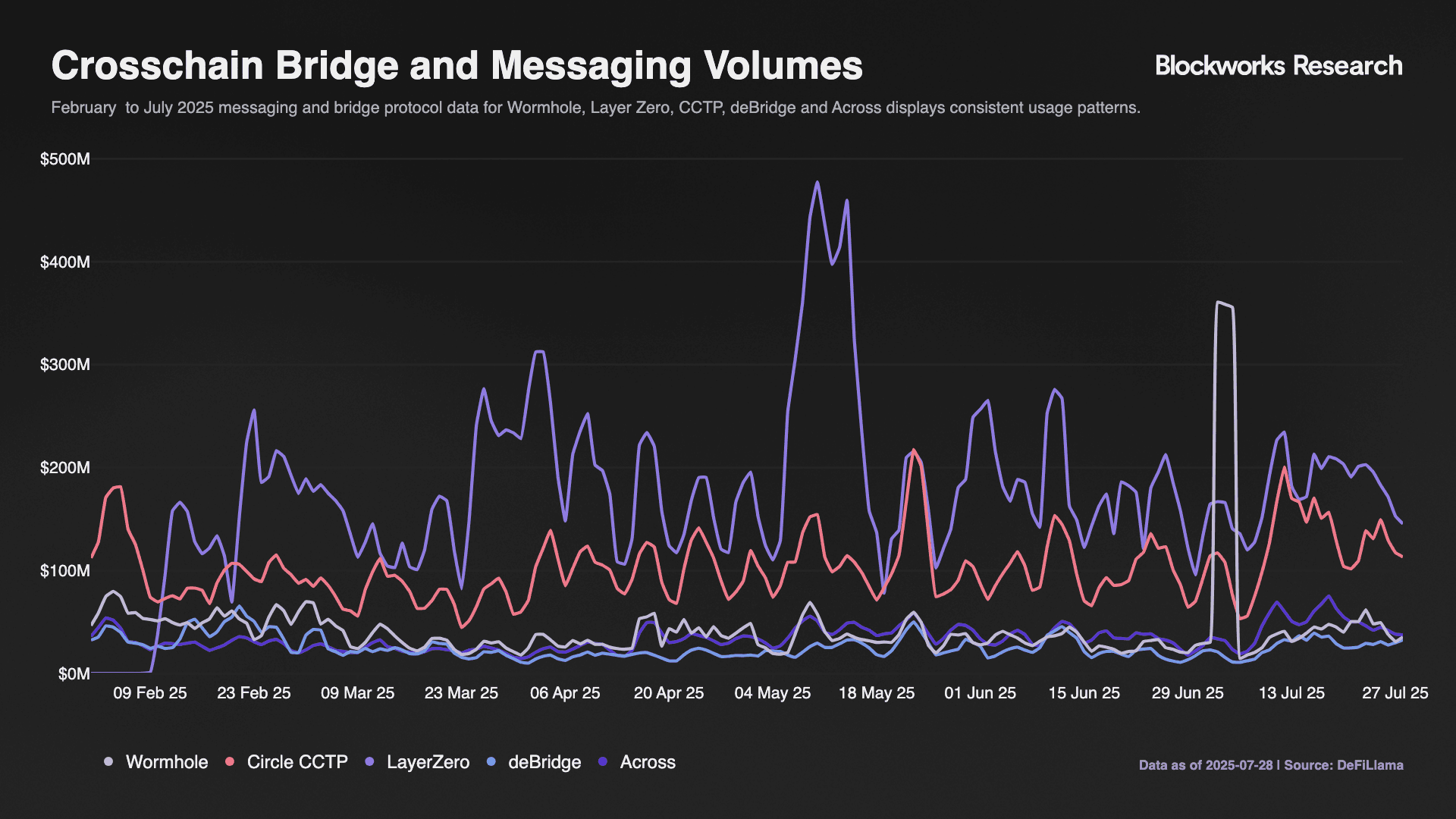
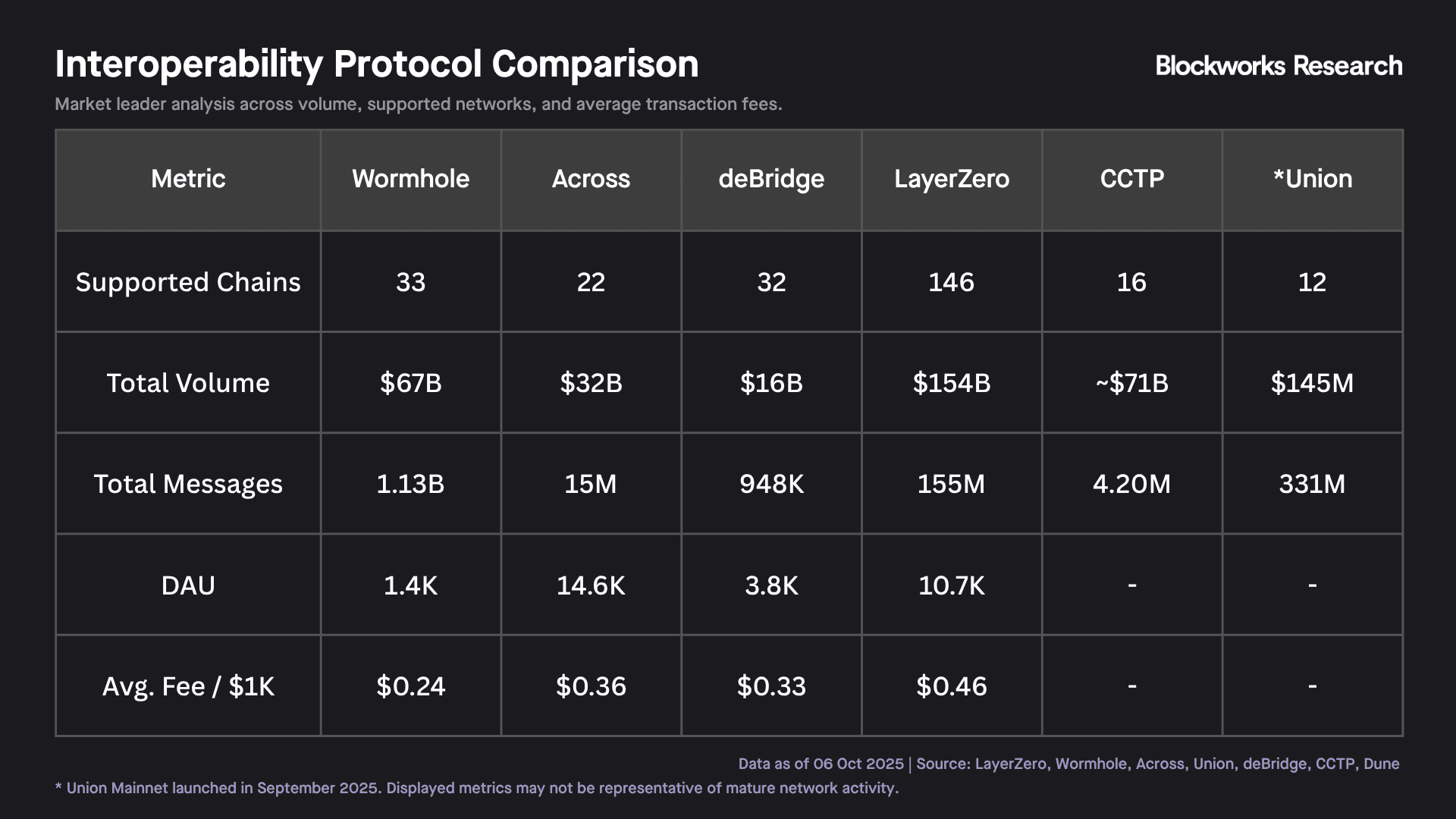
LayerZero functions as an omnichain messaging protocol. Like other interoperability solutions, it aims to serve as foundational infrastructure for crosschain communication rather than a simple bridge. Every supported network hosts an immutable endpoint contract, and applications call the source endpoint to emit a message and the destination endpoint to receive it. That simple abstraction now links 142 chains and rollups and has carried approximately >155M messages representing ~$131B in value between them, making LayerZero the most widely deployed crosschain transport layer. This extensive adoption stems partly from LayerZero's architectural simplicity. The protocol provides basic message transport without native asset handling or complex execution logic, enabling faster integration across diverse networks at the cost of reduced functionality compared to more comprehensive interoperability solutions.
Instead of imposing a single validator set, LayerZero hands security decisions to individual applications. Developers compose a Security Stack from one or more Decentralized Verifier Networks (DVNs), which can be anything from Chainlink nodes to ZK light-clients or even Axelar and Wormhole adapters, and set a quorum threshold. 52 DVNs are already live, and anyone can deploy another, eliminating vendor lock-in and letting each use case dial its own cost-versus-trust point. However, in practice, the vast majority of deployed DVNs rely on multisig configurations rather than fully decentralized or trustless verification mechanisms. While LayerZero's architecture permits zero-knowledge light clients and other trust-minimized approaches, most applications default to trusted multisig setups, meaning the protocol's theoretical security flexibility often translates to trust assumptions similar to traditional bridge architectures in actual deployment.
Execution is also modular. Once DVNs attest to a message's validity, a Permissionless Executor delivers the call to the destination chain, ensuring users never need gas on the destination and liveness no longer depends on a single relayer. This modularity puts LayerZero on a different axis from validator-governed hubs like Wormhole and Axelar or optimistic intent networks like Across. Because security and execution are pluggable, LayerZero can even wrap competitors as DVNs, acting as the interoperability layer beneath them.
LayerZero's Omnichain standards, including OFT (Omnichain Fungible Tokens) and ONFT (Omnichain Non-Fungible Tokens), enable assets to move natively without wrapped liquidity, while generalized messaging unlocks crosschain governance, restaking, and rollup-to-rollup composability. This is best exemplified by USDT0, which leverages LayerZero's OFT standard to unify USDT liquidity across chains without wrapped tokens or synthetic representations. Using a lock-and-mint mechanism anchored to Ethereum mainnet, USDT0 demonstrates how OFT standards can transform stablecoins into natively composable, cross-chain assets without liquidity fragmentation. For investors and builders, LayerZero represents less a discrete bridge and more neutral plumbing, the lower-level fabric on which other bridges, tokens, and modular rollups can operate. This positioning benefits from inclusive network effects where each new endpoint increases utility for all existing integrations.
Wormhole: Professional Validator Network and Multi-VM Support
Wormhole operates as a general-purpose message layer that links >33 heterogeneous chains spanning the EVM, Solana SVM, Move, and Cosmos ecosystems. The protocol has facilitated >$67B in cumulative value transfer through its Guardian Network, 19 professional operators including Jump Crypto and Coinbase Cloud. Once 13 of 19 Guardians sign an observation, it becomes a Verifiable Action Approval (VAA) that any contract on a destination chain can trust.
This design delivers sub-minute finality on busy routes, but its security model requires users to trust that at least 13 of these 19 entities will remain honest and resist collusion. The concentrated validator set of 19 operators is significantly smaller than typical blockchain networks and creates systemic risk. If the Guardian set becomes compromised, all routes secured by Wormhole are simultaneously vulnerable, regardless of the individual security properties of connected chains. As cumulative value transfer increases, the economic incentives for Guardian collusion or targeted compromise through social engineering, legal pressure, or physical coercion grow proportionally. This contrasts with consensus verification approaches where security is inherited from individual chain validator sets, meaning a compromise of one chain's validators affects only routes involving that specific chain, not the entire interoperability network. The Guardian model prioritizes execution speed and capital efficiency over decentralization and minimized trust assumptions, making Wormhole particularly suitable for high-frequency applications and institutional use cases where professional validation provides acceptable trust guarantees but represents a fundamental departure from cryptocurrency's trustless principles.
Wormhole's breadth across execution environments enables sophisticated crosschain applications. Native Token Transfers (NTTs) provide a framework for canonical, upgrade-friendly multichain tokens now adopted by assets from wstETH to various ecosystem tokens. Wormhole Settlement functions as an intents engine routing solver liquidity to a Solana hub, allowing capital to recycle approximately four times faster than optimistic bridges that fragment balances per route. The platform offers mature development tools including TypeScript, Rust, and Move SDKs, a Connect widget for frontend integration, and offchain WebAssembly modules for complex crosschain logic. This comprehensive developer experience has fostered ecosystem adoption beyond simple bridging to encompass crosschain governance, onchain auctions, and multichain application architectures.
Wormhole's MultiGov framework, now live on Solana, Ethereum, and major L2s, opens Guardian delegation to W-token holders who can add or remove validators through governance processes. An early stage zero-knowledge light-client path announced in 2024 is currently in internal testing and aims to make Guardian attestations cryptographically verifiable rather than merely signed, potentially narrowing the trust gap while preserving speed and capital efficiency advantages.
Across: Modular Intents & Optimistic Settlement
Across transforms bridging from a liquidity pool model into an intent market where users express desired outcomes and capital-backed relayers compete to fulfill requests. Instead of locking assets in shared pools or relying on standing validator sets, users broadcast intents specifying transfer details, and relayers fill orders instantly from their own inventories. The first relayer to fulfill a request receives reimbursement plus fees once a root-bundle of fills clears an optimistic oracle.
When users submit a transaction request, bonded relayers execute it immediately. Security relies on a 2-hour challenge window where any single honest dispute can secure settlement. Across has established dominance in the "fast-native-L2" niche by initially focusing on Ethereum-aligned chains and recently expanding to include Solana, processing >$25B across more than >15M transactions with fee and latency performance that consistently outpaces wrapped-asset and canonical rollup bridges.
This design achieves remarkable efficiency metrics. Thanks to bundled settlement and fast L2 finality, 99% of fills arrive in < 1 minute with users paying less than < $1 per ETH bridged (~3 bps at current prices), among the lowest fees in the current interop cohort. The intent model scales with relayer balance sheets rather than protocol-owned liquidity, providing significantly greater depth for supported assets.
In the Across model, fulfillment rests with professional relayers while security and verification rest with the data-worker rather than end users. After a relayer provides a fill, a data-worker submits batched transactions to UMA's optimistic oracle, and any party can dispute within the challenge window by posting a bond. Because relayers front capital from their own balance sheets, user assets are never at risk of bad fills, the worst-case outcome for a dishonest relayer is losing its bond and committed capital.
The February 2025 V3 release expanded Across beyond simple transfers through Across+ functionality that bundles arbitrary contract calls with bridge transactions, and the new Settlement layer opens the relayer network to other intent routers. This evolution positions Across as optimistic middleware that offloads complexity and risk from users to professional capital providers while maintaining fee and latency advantages over alternative approaches.
Union: Zero-Knowledge Multi-VM Transfers, GMP, & Crosschain Intents
Union addresses crosschain interoperability through consensus verification, by generating concise zero-knowledge proofs that cryptographically attest to Union's consensus state, which contains verified state proofs from connected blockchains. Built as a purpose-designed Layer 1, Union replaces multisig committees and oracle networks with mathematical proofs that can be verified across diverse execution environments. While Union primarily uses STARK-friendly curves like bn254, the protocol adapts its verification mechanism to each chain's capabilities, leveraging alternative native curves where available or falling back to direct consensus verification through manual state transition validation on chains with sufficient execution capacity but limited cryptographic primitives.
Union's architecture centers on three key components. CometBLS consensus is an evolution of Tendermint that utilizes BLS signatures and is specifically optimized for zero-knowledge proving, making Union's consensus mechanism efficiently provable in zero-knowledge circuits. The permissionless Galois prover network validates signatures in-circuit and packages them, attesting to Union's chain state in proofs that are verified in ~200K gas on Ethereum, comparable in cost to a Uniswap swap transaction. Voyager relayers permissionlessly carry data packets and proofs between source chains, Union validators, Galois provers, and destination chains.
Beyond zero-knowledge verification, Union provides comprehensive general message passing (GMP) capabilities through its ZKGM protocol. This enables arbitrary crosschain execution including contract calls, batch operations, and sophisticated token transfers with solver-based intents where smart contracts can programmatically fill orders with custom logic. The protocol supports full acknowledgements for both success and failure, eliminating the "fire-and-forget" model used in other interoperability solutions and ensuring guaranteed message delivery confirmation. Union's implementation of timeouts and acknowledgements removes stuck message resolution problems entirely, providing deterministic outcomes for all crosschain operations.
The system eliminates trusted intermediaries by reducing security assumptions to source chain consensus plus zero-knowledge soundness. Union's Groth16 trusted setup ceremony concluded with 5.8K verified contributions, the largest Groth16 ceremony in history and second only to Ethereum's KZG ceremony in total participation. However, Ethereum's KZG setup required significantly less computational complexity per contribution, making Union's achievement more technically demanding. This extensive ceremony minimizes the "honesty assumption" (the number of participants who must act honestly for the cryptographic parameters to remain secure), meaning only a single honest participant among thousands was needed to guarantee the setup's integrity. Union removes trusted third‑party actors entirely: anyone can relay, prove, or validate without permission. Union light-clients deployed on EVM, SVM, MoveVM, and CosmWasm can verify consensus proofs in single transactions, making crosschain messages as secure as the underlying blockchains involved. There are no whitelisted validator sets, economic incentives for corruption, or third-party oracles and relayers with special privileges.
Performance metrics demonstrate practical viability. Galois generates complete consensus proofs in < 7 seconds on consumer hardware, and Union's public testnets have processed >330M transfers. Union's mainnet launched on September 4, 2025, marking the transition from testnet to a live interoperability layer secured by its native U token. For latency-sensitive applications, Union layers intent markets through its partnership with Aori, enabling solvers to provide instant fills while waiting for cryptographic settlement, combining the security guarantees of zero-knowledge proofs with the speed advantages of intent-based execution.
Union's positioning as "IBC-for-everything" could make it a foundational infrastructure if adopted as default interoperability within blockchain development frameworks (such as rollup-as-a-service platforms or modular stack providers), where being the pre-integrated option would create exclusive network effects as each new chain launches with Union built-in. Rather than competing with existing bridges, Union aims to provide the trust-minimized settlement layer that other protocols can build upon, potentially capturing exclusive network effects as integration costs decrease with each additional chain.
deBridge: Validator Attestation and RFQ Liquidity
deBridge operates through two tightly coupled layers: a validator quorum for message security and the deBridge Liquidity Network (DLN) for value transfer. Each supported chain hosts a deBridgeGate contract while a rotating set of independent validators run full nodes across every supported network, signing transaction hashes that destination contracts verify through configurable thresholds.
The DLN transforms bridging economics from pooled TVL to request-for-quote (RFQ) marketplace dynamics. Market makers lock assets in DlnSource contracts and broadcast exact amounts desired on destination chains. Solvers compete to fulfill orders by posting destination tokens first, receiving user assets only after successful delivery through crosschain message confirmation. This model achieves zero-TVL operation and theoretically unlimited depth scaling with solver balance sheets rather than protocol liquidity caps.
deBridge positions itself as "Interoperability-as-a-Service" for enterprises and emerging blockchain ecosystems. Through subscription-based deBridge IaaS packages, entire Layer 1 and Layer 2 ecosystems can purchase turnkey interoperability including authenticated messaging, DLN exchange functionality, and custody services through dePort. This business-to-business approach targets game studios, brokers, and emerging rollups seeking plug-and-play crosschain capabilities without bootstrapping custom bridge infrastructure. The combination of validator-attested messaging and RFQ-style liquidity provides capital efficiency advantages over automated market makers while maintaining faster execution than optimistic bridges. Validators and market-makers monetize order flow through fee capture, while governance can dynamically adjust validator sets based on performance and reputation metrics.
CCTP: Native Burn & Mint for USDC
Circle's Cross-Chain Transfer Protocol (CCTP), launched in April 2023, provides native USDC bridging through burn-and-mint mechanics that preserve the asset's regulatory and custody properties. When users initiate transfers, source-chain USDC burns in Circle-controlled contracts, Circle's Attestation Service signs burn proofs, and anyone can submit attestations to mint equivalent native USDC on destination chains. This approach achieves 1:1 capital efficiency with no liquidity pools or wrapped tokens involved. Users inherit trust assumptions beyond typical crosschain protocols: source chain finality, Circle's attestation service availability, and Circle as the centralized issuer of USDC, though USDC users already accept this organizational trust by holding the asset.
The March 2025 V2 upgrade introduced Fast Transfer mode where over-collateralized allowances enable Circle attestation after soft finality, reducing end-to-end latency to as little as 8-20 seconds on EVM chains while maintaining fallback to standard paths during network congestion. In practice, most wallet and bridge frontends now default to Fast Transfer for sub‑minute UX, yet can fall back to the slower path during network stress without user funds ever leaving custody.
CCTP's single-asset scope belies its strategic importance. USDC commands $72B in circulation across 16 networks including Ethereum, Solana, Base, Sei, Polkadot, Hedera, and most recently Hyperliquid, making it the deepest stablecoin liquidity rail. For applications where USDC represents the desired end-state asset, CCTP offers the simplest, most liquid, and increasingly fastest crosschain option available.
The protocol's permissionless smart-contract API enables dApps to embed dollar flows without routing through third-party bridges, while institutions value the absence of upgradeable contracts on core assets. Circle's regulatory compliance and traditional finance relationships provide CCTP with a moat that pure crypto protocols cannot easily replicate, particularly for institutional and enterprise adoption requiring compliance with existing financial regulations.
Market Dynamics and Strategic Positioning
The crosschain interoperability landscape exhibits characteristics of early-stage market formation where multiple approaches compete across different dimensions rather than direct substitution. Each protocol optimizes for distinct advantages on the security-UX-cost frontier, creating opportunities for specialization and co-existence rather than winner-take-all dynamics.
Network effects vary significantly across protocols, creating different competitive moats and growth trajectories. LayerZero benefits from inclusive network effects where each new endpoint increases utility for all applications without degrading competitor value. Union's approach could generate exclusive network effects if embedded into rollup frameworks and blockchain development toolkits, making additional integrations increasingly effortless as Union becomes default infrastructure. CCTP leverages USDC's monetary network effects, where deeper liquidity and broader acceptance create self-reinforcing adoption cycles.
Switching costs create additional competitive dynamics. Wormhole's wrapped asset ecosystem generates high switching costs through ecosystem lock-in, while Across's intent-based model maintains low switching costs that benefit from best execution. LayerZero's configurable security enables medium switching costs through application-level integration requirements, and deBridge's enterprise focus builds switching costs through B2B relationship depth.
Technology differentiation remains crucial during this market formation phase. Union's zero-knowledge consensus proofs provide mathematically superior security assumptions while supporting diverse execution environments, matching or exceeding the multi-VM breadth of competitors. However, as a nascent protocol, Union requires broader adoption across chains, applications, and developer tooling to fully realize the network effects that come with being a widely integrated infrastructure provider. Across's intent optimization delivers demonstrably lower fees and faster execution on supported corridors. Wormhole's multi-VM support enables applications impossible on EVM-only protocols.
Regulatory considerations increasingly influence competitive positioning. CCTP's Circle backing provides regulatory clarity valuable for institutional adoption, while fully decentralized protocols like Union and LayerZero optimize for regulatory neutrality and censorship resistance. deBridge's enterprise focus positions it for jurisdictions requiring more traditional compliance frameworks.
Investment Framework Analysis
Platform strategy effectiveness varies based on how successfully each protocol facilitates interactions between different user groups (developers, validators, relayers, and end users) while capturing value from transaction flow.
Come-for-the-tool, stay-for-the-network dynamics appear strongest in protocols offering modular architecture. LayerZero initially attracts developers through simple messaging APIs, then retains them through expanding network utility and configurable security options. Union could follow similar patterns if developers initially adopt zero-knowledge verification for security benefits, then remain for broader ecosystem integration.
Scalability profiles differ significantly based on cost structures. LayerZero and Union can theoretically scale validator sets horizontally without proportional cost increases due to modular security and proof aggregation respectively. Wormhole's fixed Guardian set creates scaling constraints but enables predictable operational costs. Across scales with relayer balance sheets rather than protocol resources, providing theoretically unlimited capacity bounded only by market-maker capital availability.
Moat sustainability depends on ecosystem lock-in depth and technology differentiation durability. Wormhole has established data moats through wrapped asset custody and mature developer tooling, while facing challenges from zero-knowledge approaches that could obsolete trust-based validation. deBridge builds regulatory moats through enterprise relationships and compliance frameworks. Union's technology differentiation could create regulatory moats if zero-knowledge verification becomes standard for institutional adoption.
Risks and Challenges
The crosschain interoperability sector faces multi-dimensional risks spanning technical, economic, regulatory, and ecosystem categories that could impact individual protocols differently based on their architectural choices and market positioning.
Technical risks center on validator set security and execution layer vulnerabilities. Wormhole's 13-of-19 Guardian requirement creates single points of failure despite professional operator quality. Union's zero-knowledge approach introduces circuit correctness risks and prover network liveness dependencies. LayerZero's configurable security transfers risk assessment to individual applications, potentially creating inconsistent security standards across integrations. External protocol dependencies create cascading failure points that could affect multiple crosschain solutions simultaneously, while oracle manipulation risks extend beyond individual protocols to their underlying data sources and attestation mechanisms. Admin key compromises in upstream protocols could enable unauthorized fund movements across integrated systems. Different finality assumptions across chains create reorganization risks where transactions may be reversed on source chains after destination execution, and chain-specific upgrade risks where hard forks or consensus changes could temporarily break crosschain functionality.
Trusted setup requirements represent perhaps the most fundamental risk to crosschain protocols, directly contradicting cryptocurrency's foundational principle of trustless operation. Protocols like Wormhole 13-of-19 multisig configuration mean that just 13 entities hold the power to authorize arbitrary cross-chain transactions, potentially enabling theft of all funds secured by the protocol across all integrated chains. This creates systemic vulnerabilities where collusion among a relatively small group could compromise billions in user assets, while professional validators face asymmetric incentives where potential attack rewards vastly exceed any penalties for malicious behavior. Unlike traditional multisigs protecting individual protocols, crosschain validators control fund movements across entire ecosystems, amplifying the impact of any security breach through social engineering, legal pressure, or physical coercion of operators. The persistence of these trust assumptions becomes increasingly problematic as TVL grows and sophisticated attack incentives increase.
Economic risks include liquidity fragmentation and incentive sustainability. Across and deBridge depend on professional relayer and market-maker profitability to maintain service quality, creating risks if fee competition reduces operator margins below sustainable levels. Intent-based models face "optimistic challenge" risks where dispute resolution mechanisms could be gamed during high-volatility periods or network congestion. Solver and market-maker concentration creates liquidity provision risks during stressed market conditions, while cross-chain arbitrage dependencies mean protocols may experience degraded performance during periods of high volatility or network congestion when arbitrageurs withdraw. Competition for professional operators across multiple protocols could lead to service quality degradation as operators spread resources thin. Fee market dynamics could create race-to-the-bottom scenarios that compromise security through underfunded operations.
Regulatory uncertainty poses existential risks to centralized components while potentially benefiting more decentralized alternatives. Circle's attestation service faces regulatory compliance requirements that could limit CCTP availability in certain jurisdictions. Professional validator networks including Wormhole's Guardians may face KYC requirements or operational restrictions. Fully decentralized protocols like Union and permissionless aspects of LayerZero could benefit from regulatory clarity around decentralized infrastructure.
User experience complexity remains a significant adoption barrier. LayerZero's security configuration options require technical expertise that many developers and applications lack. Complex fee structures across multiple protocols make cost prediction difficult for users and treasury operations. Stuck message resolution varies dramatically across protocols, creating unpredictable failure mode, though Union's implementation of timeouts and full acknowledgements eliminates this issue by providing guaranteed message delivery confirmation rather than fire-and-forget transmission. Protocol upgrade risks where changes to core security assumptions could break existing integrations or create new attack vectors add additional complexity for developers maintaining crosschain applications.
Ecosystem coordination risks emerge from rapid technological evolution. Fork upgrades breaking endpoint compatibility could fragment network effects across protocols simultaneously. Competition between crosschain standards could delay adoption while developers await clearer winners. Integration complexity with modular rollup architectures could favor protocols with earlier ecosystem partnerships over technically superior alternatives. Critical infrastructure concentration among small operator sets creates systemic risks even in nominally decentralized protocols, while governance token concentration enables control over protocol upgrades and parameter changes that affect security assumptions. Third-party service provider risks, including RPC endpoints and indexing services, create operational vulnerabilities that protocols cannot directly control. Concentrated exposure to specific blockchain networks creates correlated risks when those networks experience downtime or technical issues, and modularity complexity where customizable security configurations could lead to misaligned incentives or improperly configured systems.
Conclusion
Rather than competing for identical use cases, leading crosschain interoperability protocols are defining distinct categories within the broader interoperability stack, each optimizing for different trust assumptions, execution requirements, and integration patterns.
For builders and treasury strategists, protocol selection should align with specific requirements rather than seeking universal solutions. LayerZero and Wormhole provide optimal flexibility for arbitrary message passing and multi-VM support through multisig-based security models that prioritize development speed and mature tooling. Across and CCTP deliver superior capital efficiency for fast, native asset movement where limited scope is acceptable. Union offers the combination of arbitrary message passing, multi-VM support, and maximum trust minimization through zero-knowledge proofs, with the primary trade-off being its relative youth as a protocol still expanding its network of connections and developer tooling. deBridge provides enterprise packaging for use cases where compliance requirements and business-to-business relationships justify a more traditional integration approach.
The sector's modularity trend suggests successful protocols will function as composable infrastructure layers rather than monolithic bridge applications. This evolution favors protocols with pluggable architectures such as LayerZero's modular security stack, Union's consensus verification framework, and Across's intent-based settlement layer that can adapt to new execution environments, regulatory requirements, and security assumptions without fundamental redesign.
We expect continued fragmentation and specialization rather than winner-take-all consolidation. The crosschain stack requires multiple layers (transport, settlement, execution, and application) where different protocols excel at distinct functions. Understanding these specializations and their intersection points will be crucial for identifying investment and integration opportunities as the multichain ecosystem matures.
This research report has been funded by Union.fi Labs. By providing this disclosure, we aim to ensure that the research reported in this document is conducted with objectivity and transparency. Blockworks Research makes the following disclosures: 1) Research Funding: The research reported in this document has been funded by Union.fi Labs. The sponsor may have input on the content of the report, but Blockworks Research maintains editorial control over the final report to retain data accuracy and objectivity. All published reports by Blockworks Research are reviewed by internal independent parties to prevent bias. 2) Researchers submit financial conflict of interest (FCOI) disclosures on a monthly basis that are reviewed by appropriate internal parties. Readers are advised to conduct their own independent research and seek the advice of a qualified financial advisor before making any investment decisions.