This research report has been funded by zcash. By providing this disclosure, we aim to ensure that the research reported in this document is conducted with objectivity and transparency. Blockworks Research makes the following disclosures: 1) Research Funding: The research reported in this document has been funded by zcash. The sponsor may have input on the content of the report, but Blockworks Research maintains editorial control over the final report to retain data accuracy and objectivity. All published reports by Blockworks Research are reviewed by internal independent parties to prevent bias. 2) Researchers submit financial conflict of interest (FCOI) disclosures on a monthly basis that are reviewed by appropriate internal parties. Readers are advised to conduct their own independent research and seek advice of qualified financial advisor before making investment decisions.
Programmable Privacy Landscape
Key Takeaways
- Institutional adoption hinges on privacy systems that combine compliance-aware features with default protections for users. Privacy is moving from niche tools to infrastructure that blends confidentiality with verifiability.
- Zcash is leading on scalability and usability for shielded payments via Tachyon, with strong compliance hooks while maintaining selective disclosures.
- Monero continues to dominate retail-level cash-like privacy, though its auditability constraints limit institutional fit.
- Ethereum and Solana are embedding privacy directly into token standards and protocol primitives, making composable, opt-in privacy part of mainstream ecosystems.
- TEE‑based confidential smart contracts enable private state and selective disclosure, but with the usual hardware‑trust tradeoffs.
- Mixers still face higher legal friction as design trends are toward compliance‑aware constructs and selective disclosure.
Overview
Privacy tech in crypto is maturing across four fronts: (1) privacy-first L1s, (2) transaction-level obfuscation via mixers/CoinJoin, (3) threshold cryptography & MPC for custody, identity, governance, and (4) application-layer privacy in DeFi, NFTs, and zk app platforms. The center of gravity is shifting from ad‑hoc tools toward systems that make privacy default while keeping results verifiable and selectively disclosable. Zcash’s proposed Tachyon pathway is the most ambitious L1 roadmap, aiming to scale fully shielded payments without degrading privacy. Ethereum, meanwhile, is steadily “snarkifying” its stack (stealth addresses, Verkle/statelessness, ubiquitous ZK proofs), with private DeFi options (e.g., Railgun) filling near‑term demand. For institutions in particular, privacy is not just a matter of user choice but of operational necessity. Without confidentiality, trading strategies, client flows, or governance actions can be exposed to competitors or hostile actors. Equally, without selective disclosure, institutions cannot satisfy regulators or auditors. True mass adoption depends on privacy systems that make transactions safe from surveillance while simultaneously allowing provable compliance when required.
As AI systems industrialize surveillance, linking financial traces, biometrics, and behavioral patterns into real-time risk scores, individual privacy shifts from preference to prerequisite. The digital economy now demands systems that are open and composable yet confidential by default and verifiable without being fully transparent. Individuals will choose privacy not to “hide,” but to preserve agency against automated inference, controlling what’s revealed, to whom, and when. This is where programmable privacy matters: Privacy-enhancing technologies turn confidentiality into a tunable parameter, enabling selective disclosure, audit receipts, and proof-of-policy compliance without surrendering raw data. As surveillance becomes cheap and ambient, default-private rails with verifiable visibility become the rational baseline for everyday payments, identity, and agentic AI, pushing privacy from a niche feature to core consumer infrastructure.
L1 Privacy
Monero
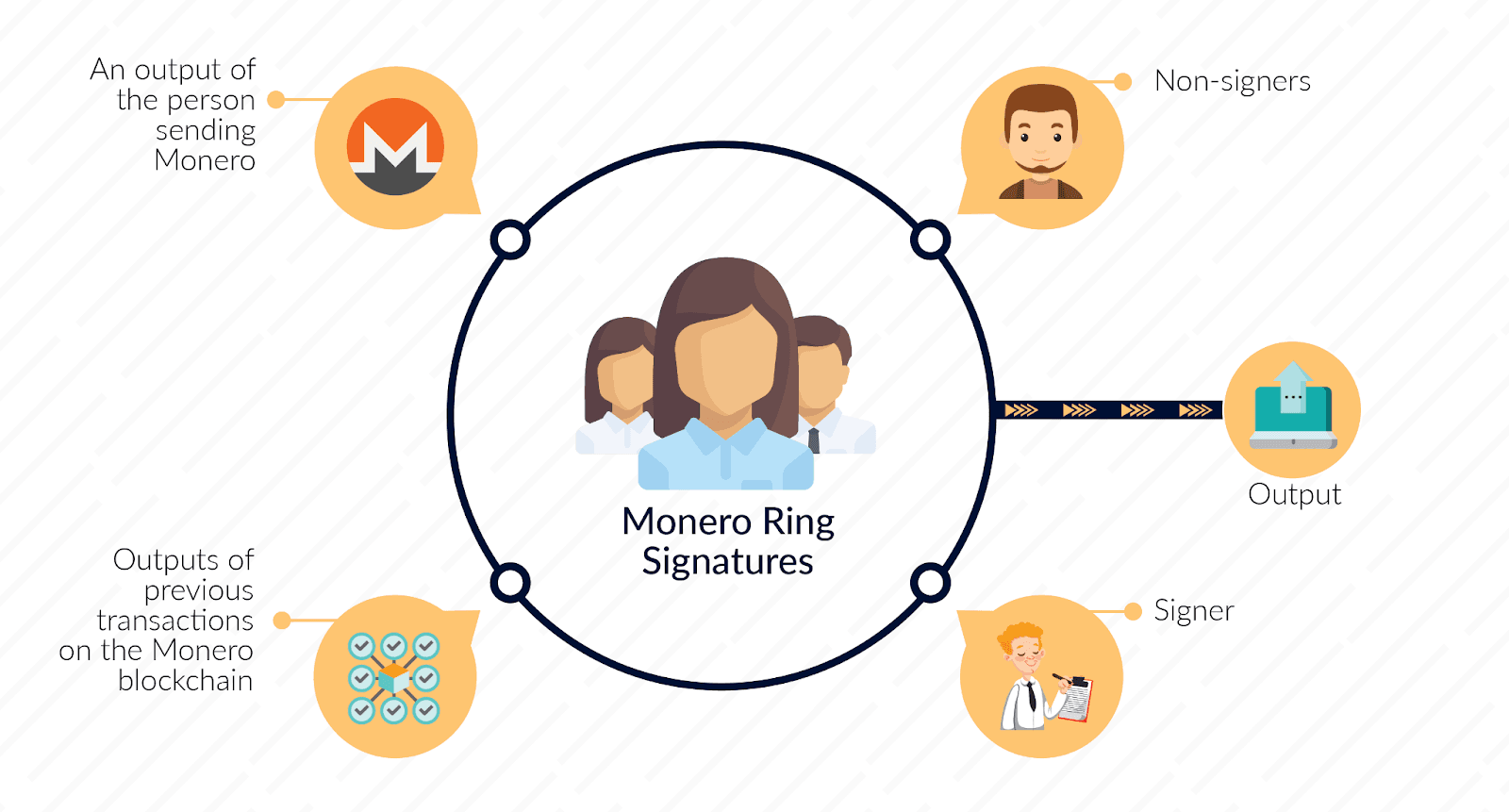
Monero is a privacy L1 using ring signatures (sender privacy), stealth addresses (receiver privacy), and RingCT (hidden amounts), with Dandelion++ for network-layer obfuscation. In practice, ring signatures mix the real input with decoys (currently 15, giving a ring size of 16). This provides plausible deniability, but research shows common decoder attacks can often reduce the anonymity set to just 2-4 viable options. Stealth addresses let senders generate one-time destinations unlinkable onchain, while RingCT ensures amounts remain hidden yet balanced.
Ongoing work like the Seraphis protocol and Jamtis address scheme aims to improve decoy selection, multisig usability, and address flexibility. However, Monero’s privacy is still heuristic in nature as observers are being “tricked” by decoys rather than blocked from seeing data entirely. Against motivated adversaries, this strategy has known weaknesses, as with all mixer-style systems. Its supply auditability is also indirect, relying on emission schedules since amounts are hidden, and view keys reveal only partial information unless paired with key-image disclosure.
Zcash
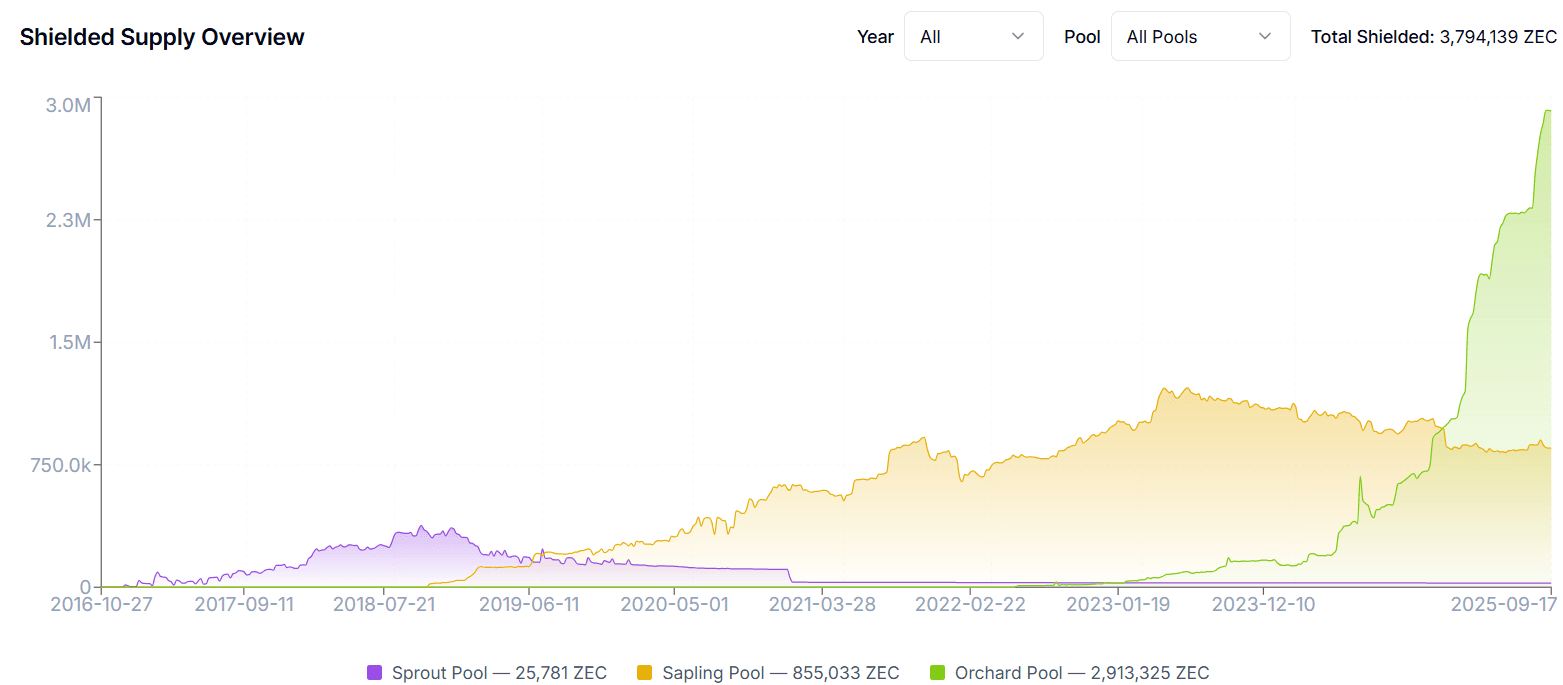
Zcash is purpose-built for payment privacy at the protocol layer. Unlike systems that rely on decoys, Zcash employs end-to-end encryption and zk-SNARK circuits to validate token transfers without revealing the sender, recipient, or amount. Only the occurrence of a transaction and its fee are visible onchain. Since the NU5 upgrade, the Orchard pool has leveraged succinct, non-interactive proofs, eliminating trusted setup and providing a scalable foundation for private payments. Shielded payloads appear indistinguishable from random bytes, which researchers call “ledger indistinguishability”, delivering stronger guarantees than Monero’s approach, which functions more like a mixer with 15 decoys. In Zcash, the effective anonymity set exceeds 5 million transactions, meaning any shielded spend could plausibly be one among millions, compared to Monero’s best-case 16-of-N model.
Beyond strong confidentiality, Zcash balances real-world needs with selective disclosure. Through Unified Addresses and Unified Viewing Keys (ZIP-316), holders can consolidate multiple receiver types into a single address and grant either incoming-only or full viewing access. This enables audits or compliance checks without compromising shielded defaults or spending authority, a design critical for exchanges, custodians, and institutions.
Recent wallet-level work has further strengthened usability and metadata protection. The Zashi wallet, developed by the core engineering team, defaults to shielded mode, effectively making Zcash private by default in practice. It adds Tor integration to protect network-layer privacy, routes transaction data through anonymized paths, and ships features like decentralized off-ramps and CrossPay, which allow shielded ZEC to be swapped directly into NEAR-supported assets and paid out privately across chains. These advances extend Zcash’s encryption guarantees beyond onchain logic and into user workflows.
Together, zk-SNARK-based shielded payments, massive and growing anonymity sets, selective disclosure tools, and private-by-default UX in Zashi position Zcash as the strongest model for scalable, compliant, and user-friendly financial privacy.
Secret Network
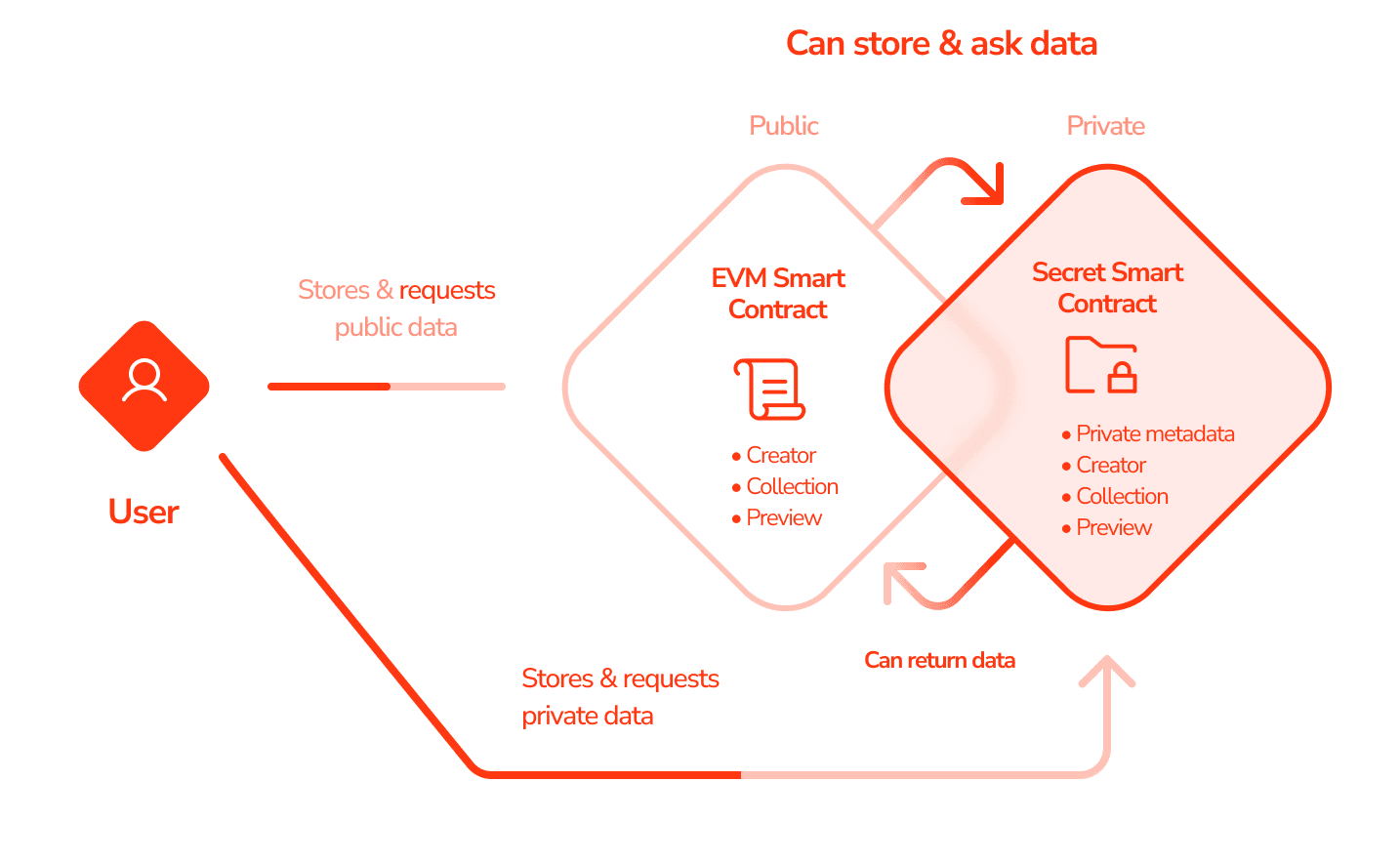
Secret Network is a smart‑contract chain where contract execution and state are encrypted inside Trusted Execution Environments (TEEs), like the Intel SGX. It supports private fungible tokens (SNIP‑20) and private NFTs (SNIP‑721) with viewing keys/permits for selective disclosure. This permits programmable privacy for app‑level logic on the L1 while private balances/metadata, gated views, and encrypted state are defaults. However, given the reliance on TEEs, trust shifts to hardware guarantees and remote attestation. Side‑channel risks and enclave supply‑chain assumptions must be taken into account.
Oasis Network (ParaTimes: Emerald, Sapphire)
Oasis is a modular L1 that separates consensus from execution. Execution happens in parallel runtimes, called ParaTimes, each optimized for different workloads. Sapphire is the confidential EVM ParaTime, that is, Solidity contracts running inside SGX enclaves with encrypted calldata/state and confidential randomness. This provides EVM familiarity and private state for straightforward private DeFi, messaging, NFTs, and gaming. Oasis also offers an Oasis Privacy Layer (OPL) for privacy add‑ons to existing EVM dapps. This setup has the same TEE assumptions as Secret, and while developer ergonomics are good, tooling must account for non‑transparent storage and enclave‑specific deployment patterns.
Ethereum “snarkifying”
Ethereum is on a multi‑year push to use ZK proofs everywhere: L2 zk‑rollups for scalability, stealth addresses (ERC‑5564) for receiver privacy, and protocol‑level proof systems (e.g., Verkle trees/stateless clients, ZK light clients) to reduce state bloat and make verification succinct. Through this, rather than bolting on mixers (discussed later), privacy becomes opt‑in and composable across wallets, apps, and infra. Stealth address standards and account abstraction-aware tooling help private receipts. Verkle/statelessness + ZK clients improve performance and unlock more private-by-default patterns. However, this is a longer-term goal, and privacy will not be the default on L1. Moreover, most activity will rely on L2s, app‑level patterns, or opt‑in standards. Tooling and UX for stealth flows (viewing keys/scan services) are still maturing.
Mixers
Tornado Cash
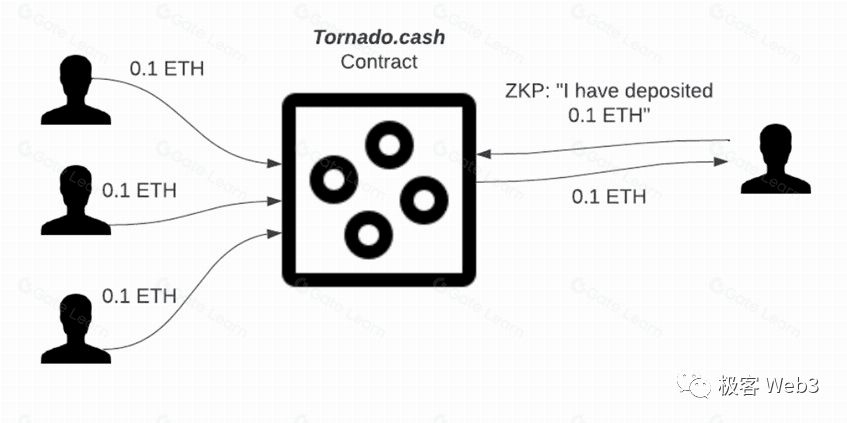
Tornado Cash is a non‑custodial mixer using deposit/withdraw Merkle commitments and zk‑SNARKs to break onchain linkability between source and destination. It illustrated the power and regulatory friction of unconditional on‑chain privacy. Post‑2022 sanctions, litigation clarified important distinctions about sanctioning immutable code. Developers faced criminal charges (with mixed outcomes), underscoring the compliance risks of universal-purpose mixers. Tornado Cash exhibited strong unlinkability at the smart‑contract level along with practical de‑anonymization vectors, including timing/amount heuristics and L1 metadata leaks (e.g., IP, gas funding). New designs are exploring selective disclosure/proof of innocence and compliance‑aware withdrawal sets ("privacy pools") to preserve legitimate privacy without shielding tainted flows.
CoinJoin
CoinJoin is a collaborative transaction pattern that combines inputs and outputs from multiple users to break deterministic links between senders and recipients. Implementations include JoinMarket, Whirlpool (Samourai), and Wasabi variants. The security model improves onchain graph privacy, but it depends heavily on liquidity, coordinator policies, uniform output amounts, and avoiding address reuse, while also requiring strong operational security practices such as Tor usage, careful change handling, and disciplined post-mix spending. From a regulatory standpoint, heightened scrutiny of commercial coordinators has forced some services to modify or shut down, while do-it-yourself or open systems like JoinMarket continue to operate but demand expert-level hygiene from users.
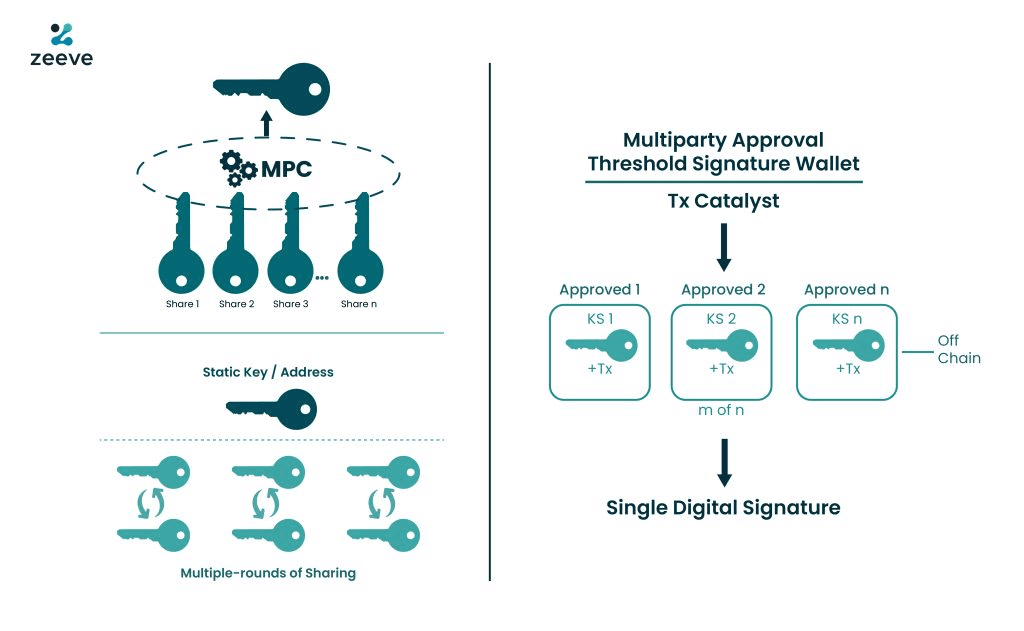
Threshold Cryptography & Multi-Party Communication
This process involves splitting secrets or signing authority across parties/devices so no single point can compromise keys or privacy. Shamir Secret Sharing (SSS) is used to break a secret into n shares, and the secret can be reconstructed with any t shares (t-of-n). This is great for backup/recovery and governance policies. Threshold Signature Schemes (TSS) and Multi‑Party Computation (MPC) signing let multiple parties jointly produce standard signatures without ever reconstructing the private key, making them suitable for hot wallets and automated policy controls. Threshold encryption and decryption allow data to be encrypted for a committee, with only t members able to decrypt, which is valuable for shielded voting, encrypted mempools, and private data releases.
These techniques underpin private custody solutions, where institutional wallet stacks use MPC/TSS for policy‑driven approvals and distributed signers, offering resilience and auditable workflows without requiring extensive HSM infrastructure. They are also used in identity systems, where threshold credentials enable multiple issuers to co‑sign certain attributes, letting users prove only what’s needed through ZK proofs, which is helpful for AML or age attestations and unlinkable logins. In governance and transaction flow, shielded voting on Snapshot and research into encrypted mempools leverage threshold encryption to keep choices hidden until tallying, reducing risks of bribery and MEV front‑running. However, these systems introduce more moving parts, such as signer coordination, distributed key generation ceremonies, and user recovery experience. Their security relies on honest‑majority assumptions and careful lifecycle management of key shares.
Application Level Privacy
Solana Extensions
Solana introduced a token extensions framework in 2024 that allows developers to attach modular features directly to SPL tokens. Several of these extensions address privacy or confidentiality. For example, Confidential Transfers integrate zero‑knowledge proofs to hide transaction amounts while preserving overall supply integrity, similar to Zcash’s approach but optimized for Solana’s parallel runtime. Extensions such as Transfer Hooks, combined with confidential metadata, open possibilities for selectively private NFTs or tokenized assets where ownership and attributes remain hidden until disclosed. Other features focus on programmable compliance, where confidential transfers still allow selective disclosure to auditors or regulators, reflecting the broader industry trend toward “compliant privacy.” Early research also points toward encrypted account states, which could support private custody workflows or institutional privacy by default. Unlike standalone mixers, Solana embeds privacy features into the token standard itself, making them composable across DeFi, payments, and NFTs without forcing developers to design full ZK systems from scratch. The tradeoffs are that adoption depends on wallet support, relayer infrastructure, and regulatory clarity. Performance is also a factor, since ZK proofs must keep up with Solana’s fast‑finality, high‑throughput model.
Private DeFi
Private DeFi projects are seeking to bring privacy to trading, lending, and asset management on existing public blockchains. One example is Railgun on Ethereum and other EVM chains, which introduces general-purpose shielded balances for ERC-20 tokens and ERC-721 NFTs. It uses zero-knowledge proofs to let users trade, lend, or transfer from a private balance while still interacting with public DEXs and aggregators through relayers. This design gives strong privacy for strategies and inventory management, while still supporting selective disclosure and auditability through view keys. Another notable effort is the Panther Protocol, which is building a privacy-enhanced DeFi stack with a focus on compliance. Its model centers on private assets called zAssets and relies on a blend of ZK proofs, relayers, and MPC to support private trading, staking, and cross-chain activity. At the same time, Panther enables selective disclosure so participants can remain compliant and provide attestations when needed. In practice, private DeFi user flows introduce new challenges. Users need to plan for gas funding in a way that doesn’t compromise privacy, and relayer trust models become critical for maintaining anonymity. There are also operational risks like doxxing through careless funding patterns, such as self-linking via L1 refills.
Risks & Policy Considerations
Regulatory approaches to crypto privacy remain fluid and differ widely across regions, creating both opportunities and risks. A key flashpoint has been mixers and privacy add-ons. Tornado Cash, sanctioned by OFAC in August 2022, became the symbol of enforcement against privacy tools, though Treasury delisted its addresses in March 2025 after appellate rulings and a policy review. This reduced headline risk but highlighted how quickly enforcement can shift. FinCEN still targets mixers, with its 2023 NPRM requiring special reporting on CVC mixing.
The European Union’s AML Regulation (AMLR) formally defines “anonymity‑enhancing coins” (AECs) and bars Crypto Asset Service Providers (CASPs) from offering anonymous accounts or services that enable obfuscation. By July 10, 2027, this could effectively prevent EU-based CASPs from supporting coins like Monero or Zcash.
The common theme is that unconditional privacy tools face the greatest scrutiny. Designs that enable selective disclosure and provable innocence are increasingly preferred, supporting compliance without full transparency. This compliance‑aware privacy aligns with U.S. and EU priorities and FATF guidance, and is likely to drive the next wave of privacy‑preserving infrastructure.
Near-term updates
Zcash Tachyon
Looking ahead, Project Tachyon represents the next leap in Zcash scalability and privacy. It is a coordinated set of protocol upgrades designed to remove long-standing bottlenecks while preserving the strong privacy guarantees that make Zcash unique. At the core of Tachyon are four breakthrough components: i) oblivious synchronization, which allows wallets to delegate blockchain scanning to untrusted services without leaking ownership information; ii) proof aggregation for Orchard via proof-carrying data (PCD), enabling many shielded payments to be verified with the efficiency of a single proof; iii) out-of-band (“liberated”) payments, which shift secret distribution offchain to cut bandwidth costs and improve indistinguishability; and iv) validator and full-node state pruning, ensuring that old state can be safely discarded without weakening security. Each track delivers incremental gains while laying the foundation for deeper architectural change.
The vision for Tachyon is both modular and ambitious. Components can land independently, providing immediate improvements, while together they open the door to orders-of-magnitude scalability for shielded payments. The Electric Coin Company has already signaled collaboration, particularly on liberated payments, reinforcing the project’s momentum. Just as the Sapling upgrade once made zk-SNARKs practical for mobile devices, Tachyon aims to redefine what is possible for private digital payments at global scale. By combining zero-knowledge proofs, proof-carrying data, and careful protocol design, Zcash is positioning itself not only to sustain privacy at scale but to accelerate toward a future where billions of users can transact with speed, efficiency, and confidentiality.
Privacy Pools
Since the launch of Privacy Pools on Ethereum in March 2025, adoption has steadily grown as the ecosystem experiments with privacy that can coexist with compliance. In the coming months, look for Association Set Providers (ASPs) moving beyond early prototypes into more sophisticated offerings, with exchanges, custodians, and analytics firms publishing machine-readable policies to define “acceptable sets” of depositors. Compliance-aware flows are also maturing, with pilots around proof receipts, audit logs, and travel-rule data payloads signaling a push toward regulatory compatibility. Watch for governance debates around ASP decentralization and cartel risk, as well as upgrades in proving systems that could make privacy-preserving transactions cheaper, faster, and usable at scale across DeFi and payments.
Conclusion
Taken together, these developments suggest the industry is converging on a model where privacy is not about “hiding” from oversight but about controlling visibility. By blending cryptographic safeguards with compliance-ready hooks, privacy tech is evolving into a baseline requirement for both individual users and institutions. This dual track, protecting users by default while enabling disclosure on demand, marks the path toward true mainstream adoption.
The information contained in this report and by Blockworks Inc. and related affiliates is for general informational purposes only and is not intended to provide legal, financial, or investment advice. The report should not be construed as an offer or solicitation to buy or sell any security, token, or financial instrument and does not represent any recommendation or endorsement of any investment or financial product or service. Blockworks Inc. and related affiliates are not registered as a securities broker-dealer or an investment advisor in any jurisdiction or country.